September 16, 2019
By Charlie Miller, CTPRP, CIPP, Ponemon Fellow, and Senior Advisor, The Santa Fe Group
In a chilling interrogation video, a suspect describes hacking into Silicon Valley startup Aupticon via a third-party weak point and an inviting Internet of Things (IoT) security hole. “They scanned most of the network,” he says matter-of-factly. “They didn’t scan the thermostat.” The hacker also notes that he scored 75 bitcoins (north of $800,000 at today’s exchange rate) for swiping and selling proprietary blueprints stored on the self-driving car company’s server.
Happily, the episode is fictional. Cisco produced this video dramatization, “Anatomy of an IoT attack,” to draw attention to the magnitude of IoT risks. Far more attentiveness and stronger IoT risk management practices are needed, judging from the Ponemon Institute’s annual study of third party IoT risk. The survey’s findings show that executives with corporate governance and risk oversight responsibilities are largely unaware of the extent to which IoT risks pose to their companies and to their third party partners.
If this comes as a surprise, you’re hardly alone.
Ponemon Institute’s research defines IoT as the physical objects – such as network-connected printers, building automation solutions or thousands of other “things” – embedded with electronics, software, sensors, and network connectivity, which enable these objects to collect, monitor, and exchange data. The 2019 survey findings are based on responses from 625 individuals who participate in corporate governance and/or risk oversight activities and who are familiar with or have responsibilities in managing third party risks associated with the use of IoT devices in their organization. All organizations that participated in this research have a third party risk management program and an enterprise risk management program.
Despite having these capabilities in place, the survey findings show that IoT risk management tends to get short shrift within companies and among organizations’ third party vendors. Some of the most notable trends the study examines include:
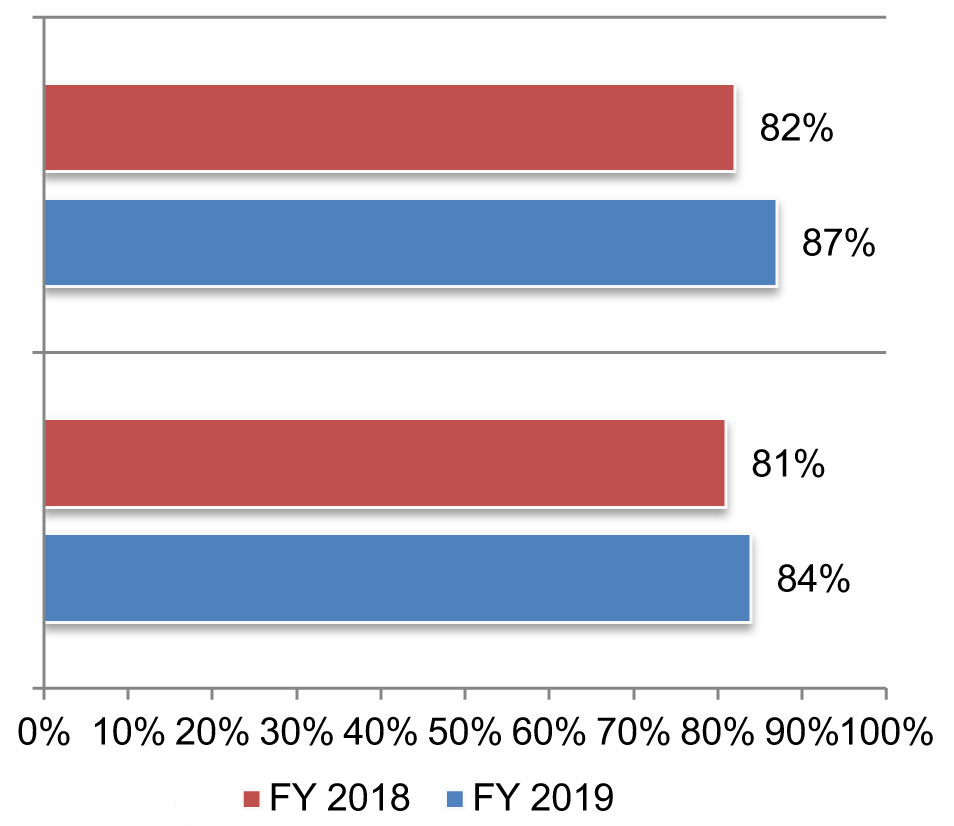
Respondents report that the likelihood of experiencing a cyberattack (top bar chart) or a data breach (bottom bar chart) caused by unsecured IoT devices or applications in the next 24 months has gone up since last year.
Those and other IoT risk management shortcomings should be addressed quickly. Fortunately, survey respondents appear aware of this need: 84 percent of respondents indicate that it is “very likely” that their company will experience a data breach caused by an IoT device or application. Plus, organizations have notched commendable progress in managing third party IoT risk during the past three years. Only one-third of respondents to our 2017 survey indicated that they evaluated IoT security and privacy practices within third parties before engaging them; this year, 40 percent of respondents say their companies do so.
Still, more progress is needed. Happily, the steps required to improve IoT risk management inside companies and among third parties are relatively straightforward. One of the most important steps involves treating IoT assets and the risks they pose in a similar manner to how organizations manage other IT assets and their attendant risks:
By drawing attention to IoT risks in the organization and among third party partners, decision-makers can help keep their companies far away from one more, rapidly expanding category of content – actual news reports of damaging hacks enabled by IoT security gaps.

Charlie Miller
Charlie Miller is responsible for expanding the Shared Assessments Third Party Risk Management membership driven program, facilitating thought leadership, industry vertical strategy groups, research studies, and regulatory and association relationships. He joined The Santa Fe Group, Shared Assessments in 2015 and has been in the third party risk space for over 13 years. A frequent speaker and recognized expert in Third Party Risk, Charlie has led vendor risk management and financial services initiatives for several global companies, including AIG, Bank of Tokyo Mitsubishi (BTMU), Merrill Lynch & Co., Inc., Deloitte, and IBM. Charlie is a distinguished Fellow of the Ponemon Institute, Certified International Privacy Professional and Certified Third Party Risk Professional.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.