APIs have helped businesses shift their service delivery models in the global pandemic. Here’s how cyber thieves have moved to capitalize on these shifts.
By Matt Keil, Cequence Security
For many companies’ consumer-oriented applications, APIs have become the connective tissue that allows development teams to rapidly deploy and update applications and services. More often than not, the web-based registration form, the mobile application login, the shopping cart or gift card balance check are all feeding a series of APIs calling to back end application and services. However, APIs are a double-edged sword as they accelerate development while also simplifying how bad actors can steal data and commit fraud.
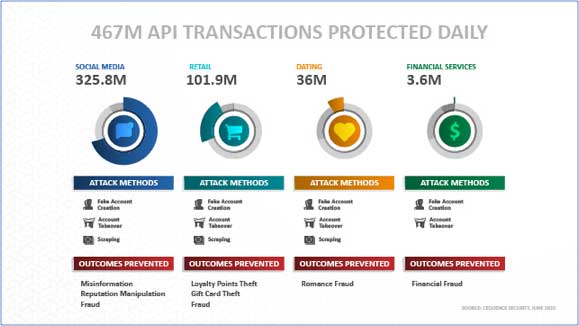
Image 1: API transactions protected daily.
Cequence has been protecting APIs from automated attacks for nearly 5 years now and a recent analysis of customers that subscribe to our threat monitoring services shows that on a given day, the Cequence Platform is protecting nearly half a billion API-based transactions.
The most common automated attacks are account takeovers, fake account creation and content scraping, however the outcomes may vary across industries. In social media, the outcome is to manipulate reputations and to spread disinformation. In dating and relationship applications, the malicious outcome is romance fraud that leads to monetary losses while in the financial services world, theft of your funds is the ultimate goal. Across every vertical, the attacks are incessant. Automated bot attacks are unlike a known vulnerability or virus that can be blocked with an IPS or AV offering. Whereas a bad actor who doesn’t find a specific application vulnerability may move on to a new target, those who are executing automated attacks are persistent, continually changing tools and tactics to achieve their end-goal of committing loyalty points fraud. These characteristics are exemplified in a summary of attack activity targeting a large retail customer.
The first of a series of campaigns began with a massive, sustained, multi-application attack of more than 23 million requests. For perspective, these attacks were 3X the total amount of traffic – both good and bad – observed in an entire normal week. The attacks observed and repelled can be broken down into 5 distinct campaigns summarized below:
Analysis of timing and traffic sources indicate that campaign #5 was a diversionary tactic to draw attention away from another part of the attack campaign – low and slow attack requests against the deprecated, legacy Web Login flow. This campaign was persistent, lasting more than 24 hours despite complete blocking on both application endpoints. Furthermore, this attack campaign attempted to fool many common browser fingerprinting techniques by reverse engineering, and trying to uniquely rotate through combinations to fool those techniques. That explosion in unique fingerprints, distributed across a long period of a day-long campaign, can be difficult to detect without proper behavioral analysis that can connect the dots, linking the campaigns and focusing on [blocking] the account takeover behavior rather than attack tool signatures.
In some customer environments, there was a dramatic uptick in attack traffic during the Covid-19 lockdown. The goal and outcome of the attack – an ATO or fake account created to execute fraud – could all be accomplished digitally. In theory, with more time on their hands due to a lockdown, the bad actors can increase their focus, which the data seems to support.
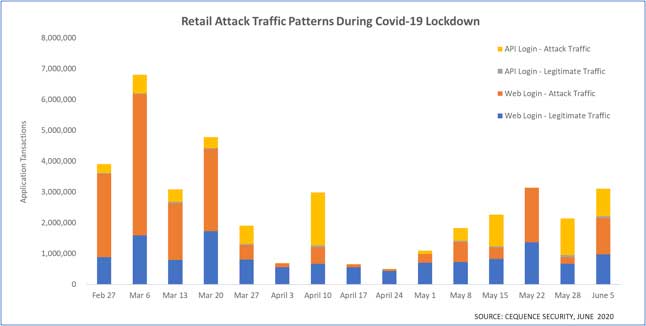
Image 2: Retail customer traffic patterns during Covid-19 shutdown.
For one of our large retail customers, we saw a very different traffic pattern. Attack traffic began to drop off at the end of March hitting lows in April (except for one week). As the nation began easing lockdown restrictions in May and allowing retail stores to open up with varied access, the attack traffic began to show an uptick. The reason? The attackers needed stores to be open. They use account takeovers to steal loyalty points and then redeem the points in the physical stores. As shown in image 2, the attack traffic peaked in March, just as the world was coming to grips with the gravity of the virus. During the height of the lockdown the attack traffic dropped significantly with a minor uptick in mid-April. As the world began to open up a bit in early May, the attack traffic began to show a slight increase. Theories for the dramatic fluctuations range from physical stores being closed, preventing the bad actors from redeeming points in-store. A separate theory is that the luxury goods sold by this retailer may not be “essential” during this health crisis. A third theory is the bad actors have gone elsewhere to look for easier attack targets.
With the recent announcement of API Sentinel, Cequence Security extends their API Security capabilities by helping organizations avoid the security gaps introduced by shadow, deprecated and non-conforming APIs with runtime inventory, risk analysis and specification conformance assessment. Learn more at cequence.ai/api-sentinel.

Matt Kiel
About the author:
Matt Keil is Director of Product Marketing for Cequence Security, and is an expert in retail sector cyber security issues and attack mitigations. Prior to joining Cequence Security, Mr. Keil was a member of the Palo Alto Networks launch team, and most recently served as Director of Product Marketing for Public Cloud. Cumulatively, Mr. Keil has approximately 20 years in enterprise network security, and was previously with NetScreen/Juniper Networks.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.