Companies building IoT and connected machines must ensure their devices are protected from these attacks. But where should they begin?
By Alan Grau, Sectigo
The growth of Industrial IoT solutions continue to expand, impacting all industrial market segments, including manufacturing, warehousing, transportation, and logistics, as well as consumer and home electronics devices.
IoT devices generate and collect tremendous amount of data, and this data must be secured against tampering and discovery. New attacks against IoT devices continue to make headlines. In many cases, the root causes of successful attacks that cause damage are devices and machines designed, built, and installed with weak or non-existent security.
Companies building IoT and connected machines must ensure their devices are protected from these attacks. But where should they begin? What steps can device manufactures take to ensure their devices are hardened?
IoT data security can only be achieved by building protection directly into the device itself. This provides a critical security layer as many connected machines are used on the edge and in the field and cannot be dependent on a corporate firewall as their sole layer of security.
Data Security Requirements
To secure the data generated by IoT devices, several critical security capabilities must be built into the device, including:
Secure Communication
In recent years, many embedded devices have added support for secure communication protocols such as TLS, DTLS, and SSH. These protocols provide a critical first level of defense against cyberattacks but leave a number of attack vectors unprotected.
Security protocols that are designed to protect against packet sniffing, man-in-the-middle attacks, replay attacks and unauthorized attempts to communicate with the device, provide a good starting point for building secure devices.
Data at Rest (DAR) Protection
IoT devices, unlike enterprise servers, are not locked away deep in a data center. Many are located “in the field” with the risk of theft or physical attack. Any sensitive data stored on these devices should be encrypted to ensure it is protected from attempts to read from the device, either by copying the data from the device, or by physically removing and reading data directly from the flash drive.
Many IoT devices do not have the computing power to support full disk encryption, but sensitive data such as credit card numbers or patient information should always be encrypted. Manufacturers need to take measures to store the encryption key in protected memory on the device. Data at Rest (DAR) protection addresses this challenge by encrypting data stored on the device, providing protection for sensitive data stored on the device.
Secure Key Storage
Secure communication protocols, data at rest protection, secure boot, and secure firmware updates all rely on encryption and certificate-based authentication. A device must have the ability to securely store the encryption keys and certificates used to encrypt data, authenticate firmware, and to support machine-to-machine authentication. If a hacker can discover the encryption keys, they can completely bypass an otherwise robust security solution. Secure key storage can be provided using a TPM or other Hardware Secure Element. If the device does not have a hardware module available, a software based secure key storage method can be utilized.
Certificates and Device Identity
PKI (Public Key Infrastructure) is a set of technologies and services for managing authentication of computer systems. PKI is based on a mechanism called a digital certificate. Digital certificates are sometimes also referred to as X.509 certificates or simply as certificates. Think of a certificate as a virtual ID card.
PKI provides the tools and methods required to issue certificates to all IoT devices on a network and to manage those certificates throughout the life of a device. A certificate can be likened to a driver’s license. It provides an identity and a set of permissions and was issued by a trusted entity. My driver’s license identifies me (Alan Grau), provides a picture to show that I am the proper bearer of the license, and defines my permissions as a driver of a motor vehicle. I am authorized to drive any standard passenger motor vehicle, but not certain commercial vehicles. And the license was issued by a trusted entity (the government of the State of Iowa).
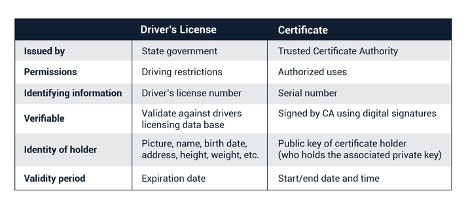
Much like a driver’s license, a digital certificate identifies the holder and must be renewed.
In many ways, a certificate is similar. A certificate is issued by a trusted entity (a certificate authority), contains permissions, and is used to identify the holder of the certificate. A driver’s license contains information allowing the holder of the license to be verified, just as a certificate contains the public key allowing it to be used only by the entity that holds the associated private key.
Without diving into the details of the public/private key cryptography technology that makes this possible, an IoT device can verify the certificate holder is the entity specified by the certificate. These services are enabled using public/private key cryptography providing the technical underpinnings of PKI. The result is that a device can verify, with cryptographic certainty, the holder of the PKI certificate is really who it claims to be and not an imposter.
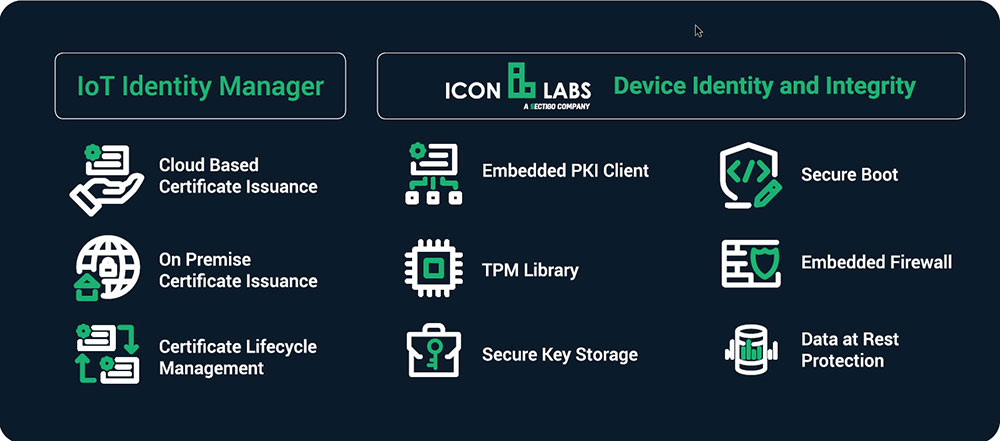
A security framework, such as Sectigo’s IoT Identity and Integrity platform, provides an integrated set of security building blocks.
Data protection for IoT devices and connected machines is no longer a nice to have—it is essential.
Cyberattacks are on the rise, worldwide cybersecurity legislation for IoT devices is becoming increasingly common (with more on the way), and network operators are beginning to require higher levels of security. To remain competitive, OEMs must address security in all of their products, no matter how small or complex.
The new rule is that Security must be built into devices from the early stages of product design.
Alan Grau, VP of IoT/Embedded Solutions, Sectigo
Alan has 25 years of experience in telecommunications and the embedded software marketplace. He is VP of IoT, Embedded Solutions at Sectigo, the world’s largest commercial Certificate Authority and provider of purpose-built, automated PKI solutions. Alan joined Sectigo in May 2019 as part of the company’s acquisition of Icon Labs, a leading provider of security software for IoT and embedded devices, where he was CTO and co-founder. He is a frequent industry speaker and blogger and holds multiple patents related to telecommunication and security.
Prior to founding Icon Labs, Alan worked for AT&T Bell Labs and Motorola. He has an MS in computer science from Northwestern University.
About Sectigo
Sectigo (https://sectigo.com) is a leading cybersecurity provider of digital identity solutions, including TLS / SSL certificates, DevOps, IoT, and enterprise-grade PKI management, as well as multi-layered web security. As the world’s largest commercial Certificate Authority with more than 700,000 customers and over 20 years of experience in online trust, Sectigo partners with organizations of all sizes to deliver automated public and private PKI solutions for securing webservers, user access, connected devices, and applications.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.