With ransomware and phishing attacks against manufacturing on the rise, manufacturers must strengthen their defenses to protect operations.

The manufacturing sector is facing a rapidly increasing number of cyber threats, with ransomware and phishing attacks leading the charge. According to the Trustwave SpiderLabs 2025 Manufacturing 2.0 Threat Report, the cost of a data breach in manufacturing has skyrocketed to $5.6 million, nearly $1 million more than the previous year. This places manufacturing well above the cross-industry average of $4.8 million, underscoring the sector’s growing appeal to cybercriminals. Despite the rising threat level, many companies remain unprepared to defend themselves.
One of the primary reasons for the increased risk is the industry’s reliance on aging, and often outdated, infrastructure. Many manufacturers continue to operate on legacy systems that cannot withstand modern cyberattacks yet still manage critical operations to this day. The situation is made worse as stolen credentials for manufacturing systems are increasingly sold on the Dark Web, allowing cybercriminals to infiltrate enterprise resource planning (ERP) and operational technology (OT) networks, which can bring entire production lines to a halt and cause widespread supply chain disruptions.
Manufacturers today face a growing security gap in their OT environments, driven largely by the sheer volume of unmanaged devices on the factory floor. Our research found that 73% of OT assets in manufacturing facilities operate without fundamental security controls like software updates, authentication requirements, or network segmentation. These devices, often essential to daily production, are frequently connected to broader networks but lack the visibility and oversight needed to detect or respond to threats. This blind spot gives attackers a clear advantage, providing multiple pathways into critical systems.
Unlike IT assets, which can be patched or updated relatively easily, OT systems often remain unchanged for years — sometimes decades — because any disruption risks halting production. But this long-standing operational mindset may lead to higher risk of a ransomware or other cyberattacks if vulnerabilities aren’t managed and resolved in old devices.
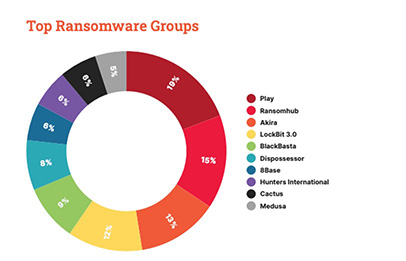
Our research found that 54% of ransomware attacks on the sector worldwide now target U.S. manufacturers, with machinery manufacturers hit the hardest, accounting for 14% of incidents. Cybercriminals know that manufacturing businesses cannot afford prolonged downtime, making them more likely to pay ransoms to restore operations quickly and essentially giving quick wins to criminals.
To protect the industry from ransomware, it’s important to have multiple layers of defense and be ready to respond quickly. Manufacturers should consider 24/7 monitoring and response services, like Managed Detection and Response (MDR), to spot and stop threats before they become serious. Separating your OT systems from your regular IT networks helps limit the damage if an attack happens. Regularly backing up important systems and data offline also ensures you can recover quickly, without needing to pay a ransom. Of course, keeping systems up to date — including both older and newer technology — can help close the security gaps that ransomware attacks often target.

Phishing remains the most common entry point for attackers, accounting for 87% of cyber incidents in manufacturing. A single click of a malicious link from a phishing email can potentially open the gateway for a hacker to steal login credentials or gain access to critical systems.
The path to cyber resilience in manufacturing starts with a shift in mindset—from treating cybersecurity as an afterthought to making it an integral part of operational strategy. Employee training is the first line of defense: manufacturers should implement regular, role-specific security awareness programs to help staff recognize phishing attempts, social engineering tactics, and unusual system behavior. Layering this with multifactor authentication (MFA) and secure email gateways can block many phishing attempts before they ever reach the inbox.
Additionally, manufacturers should collaborate with threat researchers to provide tailored threat intelligence and context around the nuances of OT security to ensure defenses evolve alongside cybercriminal tactics.
Cybersecurity is a critical differentiator for any organization today. Customers, partners, and investors increasingly expect robust security measures to protect shared data and maintain supply chain integrity. Organizations that take a proactive approach to cybersecurity are better positioned to win contracts, attract investment, and build trusted, long-term relationships. Beyond reputation, there are real financial incentives as well — manufacturers with strong security practices can reduce downtime from cyber incidents and lower operational costs.
Conversely, manufacturers that rely on outdated security practices remain prime targets for cybercriminals, facing breaches and disruptions that often far exceed the cost of modern security investments. For the manufacturers of today and tomorrow, cybersecurity is a business imperative and a vital component of maintaining competitive advantage in a security-conscious market.

About the Author:
Karl Sigler is a Security Research Manager at Trustwave SpiderLabs where he is responsible for research and analysis of current vulnerabilities, malware and threat trends. Karl and his team run the Trustwave SpiderLabs Threat Intelligence database, maintaining security feeds from internal research departments and third party threat exchange programs. His team also serves as liaison for the Microsoft MAPP program, coordinates Trustwave SpiderLabs responsible vulnerability disclosure process and maintains the IDS/IPS signature set for their MSS customers. With more than 20 years experience working in information security, Karl has presented on topics like Intrusion Analysis, Pen Testing and Computer Forensics to audiences in over 30 countries.
Read more from the author:
Securing Election Integrity in 2024: Navigating the Complex Landscape of Modern Threats | Cyber Defense Magazine, 10/7/2024
How callback phishing threatens our online safety | Security Info Watch, 12/2/2024
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.