A recent survey reveals four best practices OT leaders can adopt for securing their environments.
By Rick Peters, CISO for operational technology, North America, Fortinet
OT leaders and their respective network experts are facing new challenges regarding COVID-19 and how it will affect organizations moving forward, especially those with employees who are working remotely. The massive and sudden shift to remote work expands the threat landscape significantly, adding to the OT cybersecurity burden.
The 2020 State of Operational Technology and Cybersecurity Report from Fortinet found that organizations face challenges in terms of securing OT environments and ultimately protecting high value cyber physical assets. The 2020 report highlights a number of best practices that OT leaders and CISOs can employ to reinforce security awareness across their teams and bolster OT infrastructures with appropriate security protection.
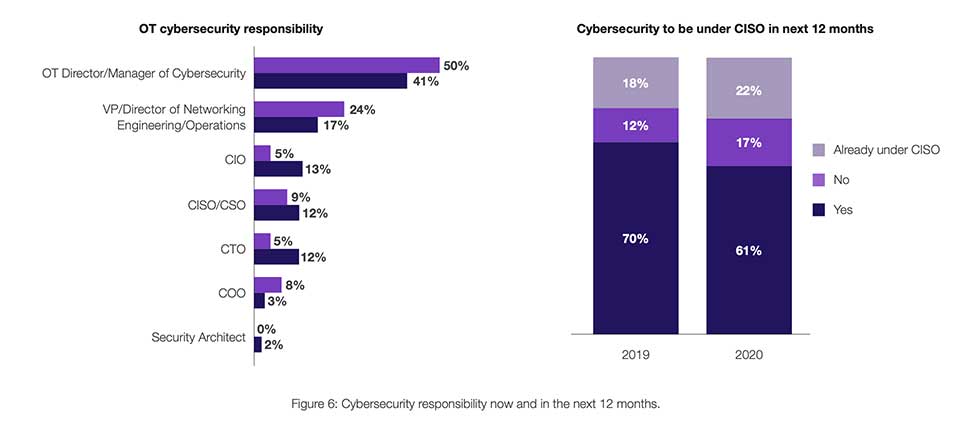
Cybersecurity responsibility now and in the next 12 months.
When it comes to OT security, maintaining the status quo is simply an unacceptable position. Despite safe and continuous operations being a top priority, nine out of 10 surveyed organizations said they’d experienced at least one OT system intrusion in the past year – that’s up from 19% in the year prior. What’s more, 68% of those organizations experienced at least three or more intrusions – up from last year’s 18%.
Attacks against OT infrastructure will only increase as malicious actors seek to execute a broad range of malicious campaigns to further disruption during challenging periods like the 2020 pandemic. These adversaries are well aware that OT environments have, for the most part, diminished the protective air gap that afforded physical separation and risk due to exposure to internet risk. An additional factor increasing the risk post IT/OT convergence is that many OT systems typically patch or upgrade infrequently leaving gaps due to inadequate security measures to compensate for this expanded attack surface. Though cybercriminals continue to evolve sophisticated attack vectors, in the case of OT environments, it’s often much simpler to repurpose well-known exploits on systems that have not been updated or patched.
In light of the increased cyber attacker attention and added digital transformation risk, how do OT leaders address these significant and expanding problems? Let’s start by examining the survey data and the corresponding measures being taken by OT organizations that are most successful. This includes:
Traditional OT leaders will probably always retain some level of partnership cybersecurity responsibility , but the clear trend is toward OT security being placed within the purview of the CISO. The CISO manages security matters for OT systems at 22% of organizations this year, up from 18% last year.
An even more revealing trend statistic is that 61% of respondents relate that they expect OT security responsibilities to be transferred to the CISO’s team in the coming year. If those changes occur as expected, the CISO’s team will manage OT security for 83% of organizations by next year. This is likely a reflection of the increasing risk of converging the IT/OT enterprise systems and the critical nature of such infrastructure for business continuity.
The 2020 Fortinet survey also revealed that 44% of respondents presently fail to track and report compliance with industry regulations. Likewise, 44% don’t track and report compliance with security standards. This practice must become that standard practice so that OT organizations maintain a security baseline characterization, proactively spot anomalies and pinpoint areas that need improvement.
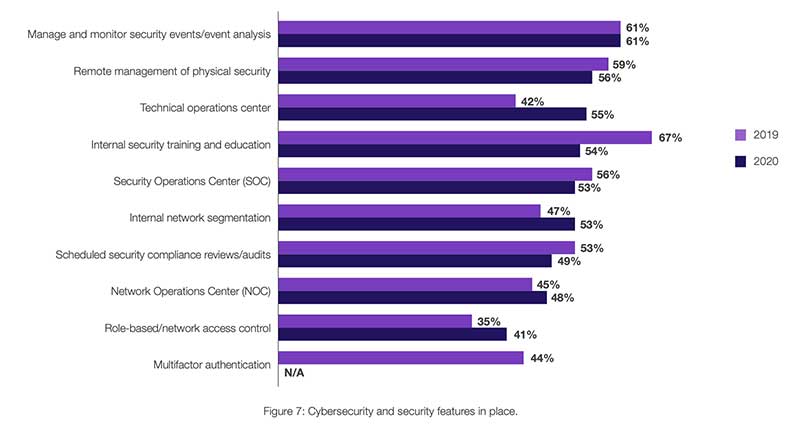
Cybersecurity and security features in place.
Organizations that ranked in the top tier are four times more likely to capture and make centrally visibility all their OT activities to the security operations team. This type of visibility is critical for effective security protection across the digitally transformed enterprise, and OT systems are no exception. Presently, 50% of top-tier respondents achieved visibility for at least half of their OT activities, with the remaining 50% achieving full visibility.
When OT organizations were asked which elements of security solutions are most important to them, security analysis, monitoring, and assessment tools were most commonly cited, with 58% ranking this in the top three features. That’s up from 44% last year. This suggests that OT leaders acknowledge the need for a more strategic, data-driven approach to security. Of note is that only 38% of respondents identified attack detection as one of the three most important features, down from 61% in 2019.
It is interesting to note that OT leaders continue to perceive that cybersecurity tools hinder their work—and thus have a negative effect on their professional success. Respondents asserted that security solutions impede operational flexibility (53%) and create more complexity (50%). This perception must change and will require the adoption of OT security services that can deliver on the requirement for transparency, speed, and scale as part of a sustainable long term solution. Consideration of an ecosystem approach to OT system security will resolve complexity with the presence of services that share intelligence and preserve the integrity of the environment from the inside-out. Absent these foundational OT security considerations, leadership will base cybersecurity investment on a perception that introduces counterintuitive thought. Complementing the OT enterprise with capability that doesn’t interfere with their decision-making process can enable the advancement of decisions that will support rather than dissuade acquisition of essential security solutions.
The modernization of OT systems that provide essential manufacturing, energy and utilities, and transportation services was already well underway by the close of 2019 as IT/OT convergence was a clear trend across the sub-sectors. The necessity for implementing best security practices to protect the IT/OT converged enterprise is clearly essential to protect high valued cyber physical assets from the point where IT meets OT and all the way down to the plant floor. The advent of additional health crisis challenges and the adoption of newly adopted remote business practices has served to expand the OT threat landscape. The good news is that OT leaders across the various industries need only to examine and mimic what successful OT organizations are advocating and implementing as best cybersecurity practices. Addressing current gaps and managing increased risk is a part of the process and requires a proactive strategy to prioritize change. Arguably, employing the strategies and ideas stated earlier in this article will enable OT leaders to forge a security strategy that addresses your organization’s primary gaps and achieve a viable OT security solution that addresses expanded threats and affording a sustainable solution for the future.

Rick Peters
About the author
Rick Peters is the CISO for Operational Technology, North America for Fortinet Inc. delivering cybersecurity defense solutions and insights for the OT/ICS/SCADA critical infrastructure environments. He is charged with overseeing growth of Fortinet’s penetration into the largest global OT marketspace. That charge entails identifying and partnering to gain traction on existing OT business campaigns as well as targeting emerging customer opportunities.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.