By Nandini Natarajan, Senior Research Analyst the Industrial Internet of Things, Frost & Sullivan
The current manufacturing industry is a by-product of several epochal revolutions in the past, including the invention of steam, electricity and automation. At the actual juncture, we are on the verge of a 4th Industrial Revolution driven by the Industrial Internet of Things (IIoT). Unlike anything in the past, this revolution will be a convergence of information technology (IT) with operational technology (OT). This confluence of technologies from the best of both worlds is expected to transform traditional manufacturing into a smarter form of manufacturing, the one that will help manufacturers to boost productivity, efficiency and revenues manifold. However, this rapid transformation of the manufacturing landscape is impeded by cyber security risks and concerns. In order to derive benefit from the Industrial Internet, manufacturers will have to move beyond boardroom discussions and approach cyber security as an essential and undeniable condition for a connected enterprise.
Traditionally the OT and the IT environments have been operating as two different silos, which is why the approach to safety in these two environments vastly differs. Threats in an OT environment could include such aspects as workforce safety, production downtime, process disruptions and anything that can cause physical damage to plant assets and workforce. Traditional IT-based cyber security solutions were not designed to handle these kinds of OT scenarios. In fact, an IT organization’s lack of expertise in manufacturing is one of the major setbacks in failing to address the security needs of an industrial unit. Towards delivering an effective security solution, both the IT and the OT environments will require very close collaboration to assess vulnerable points in their ecosystem. These vulnerabilities must be prioritized and security gaps have to be closed.
Whether or not IT organizations have deep domain expertise, the market is flooded with participants who claim to deliver the best counter mechanisms for impending cyber threats. While it may become impractical for us to individually assess them all, the following recommendations highlight what pace setters have been doing differently in industrial cyber security. The rest of us could consider adopting these approaches within our realms of industrial operations:
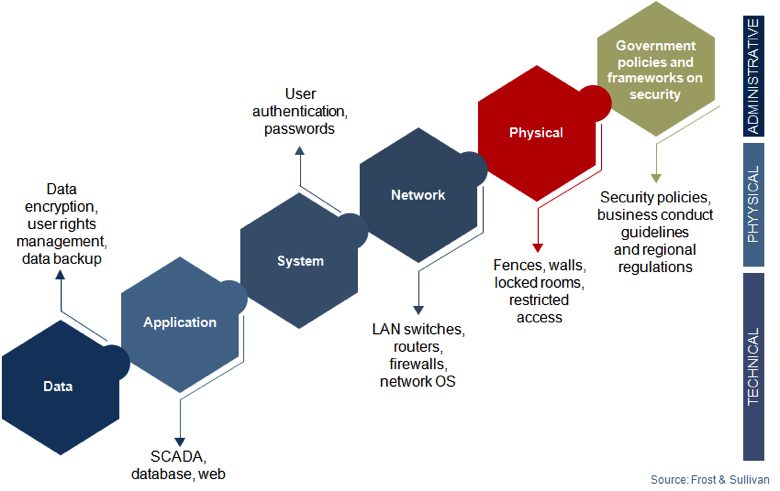
Defense in depth security model of a manufacturing unit
Controlling security breaches at different levels can help prevent loss of control over production. Following such a comprehensive security approach to the dynamic needs of the industry will finally get its due from the industrial world. Finally, the evolution of new manufacturing trends like IIoT will help to drive cyber security beyond just theory and make it a tangible, real and quintessential part of production environments in the years to come.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.