Critical infrastructure in the crosshairs: operational technology vulnerabilities jump 88%.
SAN JOSE, Calif. – Threat intelligence analysts at Skybox Research Lab uncovered a 42% increase in new ransomware programs targeting known vulnerabilities in 2021. Today, the Silicon Valley cybersecurity company released its annual 2022 Vulnerability and Threat Trends Report, revealing how quickly cybercriminals capitalize on new security weaknesses – shrinking the window that organizations have to remediate vulnerabilities ahead of an attack.
With 20,175 new vulnerabilities published in 2021, Skybox Research Lab witnessed the most vulnerabilities ever reported in a single year. And these new vulnerabilities are just the tip of the iceberg. The total number of vulnerabilities published over the last 10 years reached 166,938 in 2021 — a three-fold increase over a decade.
These cumulative vulnerabilities, piling up year after year, represent an enormous aggregate risk, and they’ve left organizations struggling with a mountain of cybersecurity debt. As the U.S. Cybersecurity and Infrastructure Security Agency (CISA) highlights in its Top Routinely Exploited Vulnerabilities list, threat actors are routinely exploiting publicly disclosed vulnerabilities from years past.
“The sheer volume of accumulated risks — hundreds of thousands or even millions of vulnerability instances within organizations — means they can’t possibly patch all of them. To prevent cybersecurity incidents, it is critical to prioritize exposed vulnerabilities that could cause the most significant disruption,” said Ran Abramson, threat intelligence analyst, Skybox Research Lab. “Then, apply appropriate remediation options including configuration changes or network segmentation to eliminate risk, even before patches are applied or in cases where patches aren’t available.”
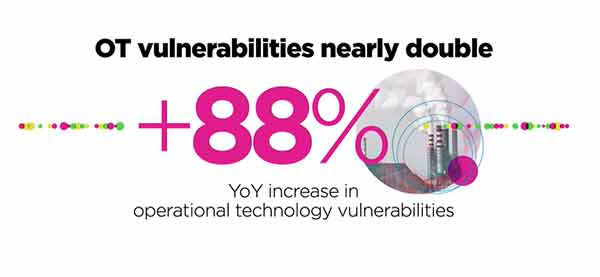
Operational technology (OT) vulnerabilities jumped 88%,1 which are used to attack critical infrastructure and expose vital systems to potentially devastating breaches. OT systems support energy, water, transportation, environmental control systems, and other essential equipment. Attacks on these vital assets can inflict severe economic damage and even endanger public health and safety.
As OT and IT networks converge, threat actors are increasingly exploiting vulnerabilities in one environment to reach assets in the other. Many OT attacks begin with an IT breach, followed by lateral movement to access OT equipment. Conversely, intruders may use OT systems as steppingstones to IT networks, where they can deliver malicious payloads, exfiltrate data, launch ransomware attacks, and conduct other exploits. Increasingly, malware is designed to exploit both IT and OT resources.
As new vulnerabilities appeared in 2021, threat actors wasted no time taking advantage of them. One hundred sixty-eight vulnerabilities that published in 2021 were promptly exploited in the wild within 12 months — 24% more than the number of vulnerabilities published and subsequently exploited in 2020. In other words, threat actors and malware developers are getting better at weaponizing recent vulnerabilities.
This puts security teams in a squeeze, reducing the time between the initial discovery of vulnerabilities and the emergence of active exploits targeting them. That shrinking window to remediate known exploits means that proactive approaches to vulnerability management are more essential than ever.
New cryptojacking programs targeting known vulnerabilities increased by 75% year over year, along with the 42% rise in ransomware. Both cases illustrate how the malware industry is getting better at leveraging emerging business opportunities, providing a range of tools and services used by seasoned cybercriminals and inexperienced newbies alike.
Cybercriminals target easy money, and their malware-as-a-service packages exploit the most widespread vulnerabilities. The largest number of malware programs in 2021 targeted Log4Shell, Microsoft Exchange Server vulnerabilities, and a Pulse Connect Server vulnerability.
According to Forrester Research: “CISOs dread one question above all from their boards: ‘Are we safe?’ Boards ask this question because they want to know if security leaders are investing in the right areas and investing enough in security to meet their tolerance for financial loss experienced due to a cyber risk. CISOs, however, have struggled to answer this question for a long time, historically relying on qualitative approaches such as ordinal scoring mechanisms and 5×5 heatmaps which are based on subjective expert judgment and opinion.”2
To standardize on a common risk language, security teams need an objective framework for gauging the actual risk that any given vulnerability poses to their organization. This requires the use of a rigorous scoring system that can be used to prioritize remediation efforts and allocate precious resources where they’re most needed. That means calculating risk scores for assets based on four critical variables:
“Exposure analysis is paramount, yet it’s missing from conventional risk scoring approaches,” added Abramson. “Exposure analysis identifies exploitable vulnerabilities and correlates this data with an enterprise’s unique network configurations and security controls to determine if the system is potentially open to a cyberattack.”
Read the 2022 Vulnerability and Threat Trends Report.
About Skybox Research Lab
The Skybox Security threat intelligence division continuously monitors dozens of security sources, tracking and analyzing tens of thousands of vulnerabilities on thousands of products, along with the latest data on exploits and malware taking advantage of these vulnerabilities. Drawing on this research, Skybox Research Lab identifies the vulnerabilities most likely to impact our customers’ networks and assets. These vulnerabilities are combined with critical contextual information on whether and how the vulnerability has been exploited, the prevalence of the vulnerability, the malware that exploits it, the damage it can inflict, and optimal approaches to remediation. All of this information is incorporated in a proprietary database used in our product and by Skybox customers.
https://www.skyboxsecurity.com
Media Contact
Ashley Nakano
Corporate Communications Director
media-relations@skyboxsecurity.com
1 The OT vulnerabilities in this report are based on new vulnerabilities shared by CISA in 2021.
2 Transform Cyber Risk Management with Cyber Risk Quantification, Forrester Research, Inc., January 27, 2022.
© 2022 Skybox Security, Inc. All rights reserved. Skybox Security and the Skybox Security logo are either registered trademarks or trademarks of Skybox Security, Inc., in the United States and/or other countries. All other trademarks are the property of their respective owners. Product specifications subject to change at any time without prior notice.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.