5G and edge computing are transforming manufacturing factories in areas such as worker safety, security, and quality.
by Flavio Bonomi, advisor to the CEO, Lynx Software Technologies
The old saying “build a better mousetrap and the world will beat a path to your door” is often cited as a metaphor for the transformative power of innovation. Today that saying might as well be “build a better manufacturing plant and the data will beat a path to your door.” The increasing adoption of private 5G wireless networks, along with the accepted concept of edge computing, is empowering manufacturers with the ability to gain actionable insights in real-time that are transforming the industry in areas including security, worker safety and quality.
In a study conducted just prior to the pandemic by Deloitte and the Manufacturer’s Alliance for Productivity and Innovation (MAPI), respondents cited double-digit gains in labor productivity (12%), factory capacity utilization (11%) and total production output (10%) during the previous three years as a result of their smart factory initiatives. With 5G, these trailblazing manufacturers will have the ability to connect more devices and collect more and new types of data, which will enable them to remain at the forefront of the industry.
When paired, 5G and edge computing provide the foundational infrastructure for new ways of operating. While Wi-Fi is powerful enough to support multiple devices in a home or office, it was never well-suited for the hundreds or thousands of sensors and other devices in a manufacturing or warehouse setting. Similarly, cabled connections have obvious restrictions for machines on the move. 5G is increasingly enabling industrial organizations to take advantage of powerful edge computing to bridge the traditional gap between digital and physical operations.
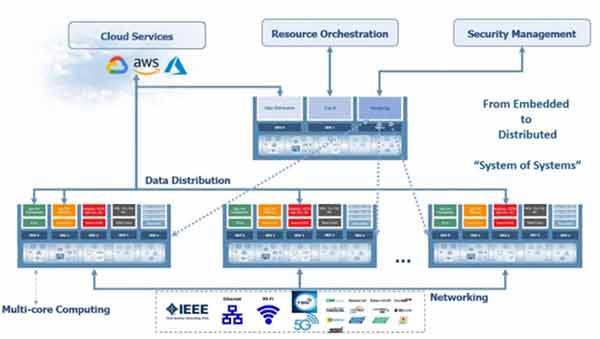
The Deloitte study also found that early adopters of AI in manufacturing were piloting an average of 10 different initiatives. These ranged from energy conservation and resource allocation to robotic process automation to collaborative engineering and digital twins. Due to supply chain disruptions and raw material shortages over the past two years, one area with a clear impact on the bottom line is quality sensing and the detection of imperfect or otherwise defective products.
This real-time equipment monitoring requires cameras and nuanced AI analytics based on data models that can train the system to quickly “see” product flaws and remove them from the production line, and alert engineers who can adjust specifications or recalibrate machinery to correct the root cause. According to Deloitte and our own research, these systems can reduce the shipment of defective products by up to 10x.
Designing this type of edge computing solution requires cloud-like functionality on the camera sensor. While there are a number of ways to achieve this, the most efficient approach is to use containerized software services that enable:
As with any operationally critical system, security and safety concerns need to be addressed. One of the big system architecture challenges is how to combine an organization’s IT networks with operational technology (OT) while ensuring worker safety, product quality and system availability/reliability are maintained.
Any edge solution deployed in an industrial setting needs to be configured as a “least privilege model” in which applications are only granted access to the system resources they need to perform their function, and nothing more. These virtualized servers are effectively sequestering the OT network from other parts of the organization’s network that are accessible to the internet.
These permissions need to be immutable to avoid a reconfiguration (either malicious or accidental) that exposes a system’s “crown jewels”. Think about the system as a house. All system elements are assigned to different “rooms” and each of them is locked so in the event that one specific area is compromised, access is limited.
There has been a significant uptick in focus on making systems immune to attack. A more prudent approach is to recognize that no system is immune to attack; more efforts need to be spent on
Artificial intelligence is starting to be applied here to learn the “normal” behavior of an embedded system and recommend when a meaningful change in the system needs to be evaluated as a potential security risk.
Like other industrial infrastructure, manufacturing machinery and software are often deployed for 10-15-20 years – or longer. System designers need to future-proof their solutions so they are architected to remain impenetrable from any attack from any internal or external source for decades. Here again, containerized software can allow for segments of the software to be updated or upgraded without the need to replace the entire system.
In addition to complicating supply chain issues, the pandemic also accelerated the need for new safety measures designed to minimize human interaction and exposure. In response to this need, some manufacturers deployed collaborative robots – “cobots” for short – to ensure their production facilities remained online to keep up with customer demand.
Cobots essentially interact with human workers in a shared workspace and are quite different from traditional industrial machinery, which typically works independently of the human workforce. As cobots find their places on the factory floor, ensuring the safety of their human coworkers is paramount. This is a complex issue that is not easily solved. A private 5G network, however, can provide powerful bandwidth for the cobot to serve as an “edge computer” and make split-second decisions in reaction to the behavior of the people beside them on the line.
The adoption of private 5G networks by today’s early adopters in manufacturing provides a sneak peek at the factory of the future. As transformational and exciting as the capabilities and real-time analytics might be, systems designers need to maintain the same rigor and attention toward the safety and security of these networks as is applied to the organization’s core computing systems – if not more.

Flavio Bonomi is advisor to the CEO at Lynx Software Technologies.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.