The DoD’s major change to the Cybersecurity Maturity Model Certification (CMMC) program is having an impact on government contractors.

by Matt Gilbert, CISA, CRISC, Principal at Baker Tilly
After conducting an internal review, the Department of Defense (DoD) recently announced a major change to the Cybersecurity Maturity Model Certification (CMMC) program.
According to the DoD, the updated framework, now called CMMC 2.0, will:
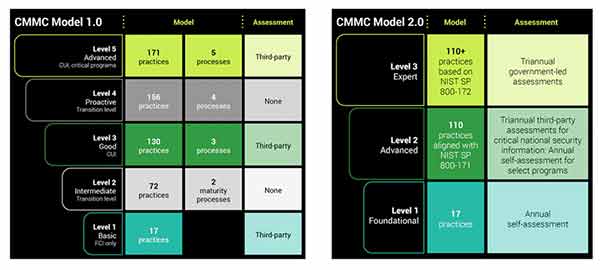
CMMC 1.0 TO CMMC 2.0 COMPARISON ©BAKER TILLY
Many organizations are now wondering what is changing with CMMC requirements and what stays the same? What key questions still need to be answered?
Much of CMMC remains the same; however, many government contractors need to evaluate and understand these five key changes:
The decision tree and notes below can provide some further insight into how CMMC 2.0 may impact your organization.
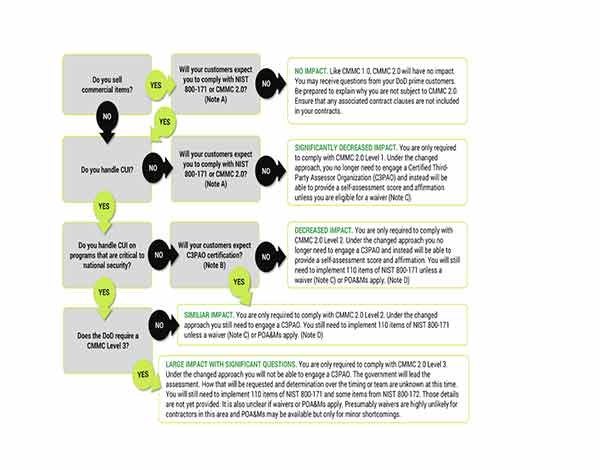
CMMC 2.0 Decision Tree
Graphic and notes provided by Baker Tilly
Note A – While the DoD may not require CMMC 2.0, some prime contractors (prime) are pushing their supply chain to comply. Doing so makes it easier for the prime. If all preferred providers are CMMC 2.0 Level 2 or higher, they have less to worry about when sharing CUI. This behavior can drive more organizations to require CMMC 2.0 certifications.
Note B – Similar to Note A, if primes require Certified Third-Party Assessor Organization (C3PAO) assessments and not self-assessments that may drive organizations to seek certification who otherwise would not. This again would make it easier for the prime because they would not need to make the distinctions or fulfill/address requirements in contracts to understand when a self-assessment is permitted.
Note C – Waivers appear to be very rare. If you have multiple contracts or plan to have multiple contracts in the future, it is unlikely that all would be eligible for a waiver.
Note D – POA&Ms will only apply to minor items. While this might save you from a failure if you do not have one item in place, it does not mean you can be certified without addressing some of the larger, more costly aspects of NIST 800-171.
While the changes to CMMC 2.0 seem like a major reduction in effort at first, further examination shows that it does not change much of the original burden for most contractors. A small percentage will avoid C3PAO certification or otherwise obtain waivers, however the vast majority of organizations will still need to properly prepare for CMMC to win future contracts with the DoD.

Matt Gilbert
Matt Gilbert is a principal in Baker Tilly’s risk advisory practice and leads the Cybersecurity Maturity Model Certification (CMMC) and Government Contractor IT Risk suite of services.
www.bakertilly.com
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.