Ensuring security is built in at device design, across the supply chain and through device lifecycle is key to building trustworthy devices.
The security of connected IoT is complex, depending on how connected devices are used and the vulnerabilities and threat vectors that could compromise them. Billions of connected devices exist in the world today, with a growing number used in industrial control and critical infrastructure. When it comes to connected transportation like aviation and rail systems, infrastructure like power grids and water systems and even healthcare delivery devices like pacemakers, the connected components these systems rely on could come with life impacting consequences if they are compromised.
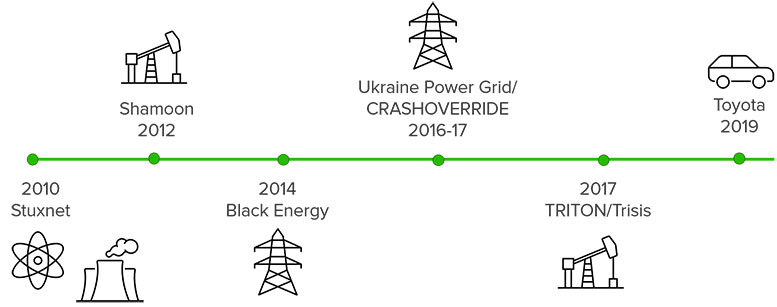
Industrial cybersecurity over the years.
When it comes to IoT device security, it’s not just about protecting the endpoint once a device is activated. Ensuring security is built in at device design, manufacturing, activation and through the device lifecycle is critical and involves multiple stakeholders throughout, especially across the supply chain.
The proliferation of new, connected devices means that the worlds of traditional IT networking and security are colliding. Traditionally, device design has lived with product developers and mechanical and electrical engineers – skilled professionals who are exceptional at creating product to meet performance specifications, but who are not usually well versed in security and the vulnerabilities that can compromise a device’s safety and reliability. A significant number of connected devices in use today are legacy, designed and deployed when security was an afterthought or last-minute consideration. As a result, attackers have been able to directly and indirectly compromise and exploit connected devices in several ways, often successfully gaining lateral access to a larger network as part of their campaign.
In many cases, once a device is compromised, attackers can do things like steal or sign code to implement unauthorized firmware updates or steal software for counterfeit device manufacturing.
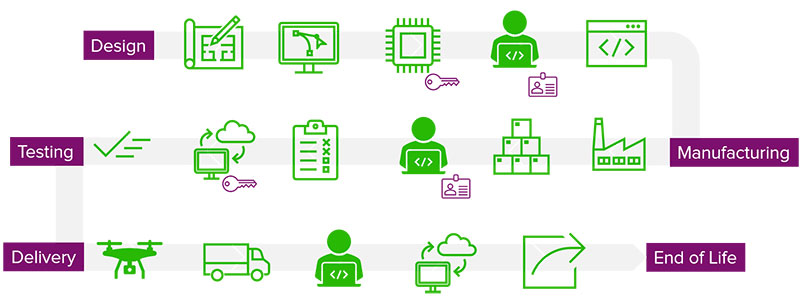
What is zero trust manufacturing.
Several years ago, Forrester Research coined the term, “zero trust networking”, an architecture that ensures end users and devices can access a network securely through access controls, authentication and micro-segmentation. It relies on basic checkpoints to verify a user’s identity but fails to define how or why the system can trust that identity and credentials. Zero trust manufacturing picks up where zero trust networking stops, ensuring the integrity and trustworthiness of the systems and devices the network accesses. It is an end-to end process that can be used to design, manufacture, test and deliver trustworthy products from the manufacturer to the operator and through the device lifecycle.
Public Key Infrastructure (PKI) serves as an underlying foundation through the process, utilizing and safely storing everything from signed code to secure digital keys and certificates. When crypto-agile best practices are leveraged, PKI can automate the process of managing digital assets to ensure they are always up to date. Without PKI, a lack of management means that untracked digital keys and certificates are rarely rotated, ultimately making the device less secure.
Regardless of where you fit in the supply chain, the adoption of zero trust manufacturing best practices ensures trust is established and maintained from the time a product enters design to the time it leaves the manufacturing floor – and beyond.
With any embedded device, the first step is to choose the crypto library that fits the device’s needs, its encryption requirements and factory provisioning. Next, initial key and certificate creation, sometimes referred to as a birth certificate or bootstrap certificate, establishes the device’s initial identity certificate.
In industrial or infrastructure system monitoring (like a factory or power plant), an agent can be used for on-device key generation to leverage embedded security functions on the device itself, establishing trusted interaction between the agent and the system. In this case, only the device knows its own identity, making certificate creation process more secure.
When implementing zero trust manufacturing, five guiding principles can help establish the process across the supply chain:
At the end of the day, zero trust manufacturing and zero trust manufacturing architecture must be at the center of how manufacturers and the supply chain think about securing and building trustworthy and secure connected devices.

Ellen Boehm
Ellen Boehm has over 15 years’ experience in leading new product development with a focus on IoT and connected products in lighting controls, smart cities, connected buildings and smart home technology. Currently, she is senior director of IoT product management at Keyfactor, a leading provider of secure digital identity management solutions. For more information visit: www.keyfactor.com or follow @Keyfactor on Twitter and LinkedIn.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.