Cyber is everywhere in manufacturing. Framing risks in use cases can help identify unknown vulnerabilities.
By Sean Peasley, Ramsey Hajj, and Jason Hunt
Deloitte and the Manufacturers Alliance for Productivity and Innovation (MAPI) have been formally studying cybersecurity and associated risks since 2016. Our collaborative studies have identified growing awareness of the potential cyber threats related to smart factory initiatives. However, many manufacturers have had difficulties advancing their cyber risk management capabilities. In the 2019 study, forty-eight percent of manufacturers surveyed identified operational risks, which include cybersecurity, as the greatest danger to smart factory initiatives. The risks for cyberattacks are substantial and can be far-reaching in a smart factory environment, exposing people, technology, physical processes, and intellectual property.
Today, cyber is everywhere in manufacturing, even more so with the introduction of digital and smart technologies. In fact, the manufacturing industry is often considered among the most frequently targeted industries for cyberattacks. Every employee, every partner, every device or piece of machinery, and even every finished product can bring with it the potential for cyber risk. And, while 8 in 10 manufacturers surveyed have at least some capabilities to detect and respond to cyber threats, one in four has not performed a cyber risk maturity assessment in the past year. This gap could be exposing manufacturers to more vulnerabilities than they are prepared for – or even aware of.
Some surveyed manufacturers haven’t performed a cyber risk assessment in the past year
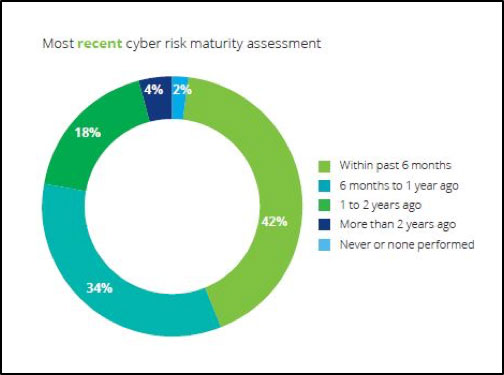
Source: 2019 Deloitte and MAPI Smart Factory Study
While manufacturers work on enhancing their digital maturity, aspects of building cyber resilience may lag. To overcome this situation, manufacturers can approach cyber risks through the lens of the smart factory use cases. These use cases are a common way in which manufacturers launch smart factory initiatives. Smart factory use cases combine advanced technologies with process innovation to address a specific business challenge or opportunity. Below are eight popular use cases that many manufacturers currently adopt in their smart factory initiatives.
To understand the considerations for cybersecurity at the smart factory use case level, it can be helpful to look at a few representative examples. Below are two smart factory use cases explained through a cyber lens. Each explains the capability that the use case enables, identifies data types and owners as well as entry points and potential threats/vulnerabilities, followed by specific cybersecurity considerations. For an in-depth look at six of the smart factory use cases, visit the full report.
| Capability | Predictive maintenance, AR to assist maintenance personnel, sensor-enabled asset monitoring |
| Data types | Machine-specific performance data, OEE data, maintenance schedule and repair history |
| Data owners | Operations and production team; maintenance and repair team |
| Entry points | Assets on production lines; maintenance staff and third parties |
| Threats/vulnerabilities | Access to OT environment via software that may have been developed without considering security needs. AR glasses could be compromised. Cyberattackers could gain visibility to factory asset data, including product and client information, or could disrupt production and damage assets. |
| Cybersecurity considerations | Adopt a risk-based approach rather than compliance-based approach.
Approach security considering defense-in-depth needs with a consistent program and structure —educating personnel, gaining visibility across the sites, segmenting the network, monitoring for abnormal behavior, and having a capability to respond/recover. Continuously assess entry points, motivation, and vehicles to execute an attack to enable the organization’s technical teams to build operational response capabilities.
|
| Capability | Virtual models of a physical product (or assembly) to run simulations, predict product performance, and make iterative design modifications |
| Data types | Product configurations, materials, other intellectual property (IP), customer usage data, repair and warranty data, quality data |
| Data owners | Engineering and design department, product management, after-market service, quality control, suppliers |
| Entry points | Hardware including AR glasses, laptops, VR caves; software applications, databases, and analytics tools; network and cloud |
| Threats/vulnerabilities | Network-enabled engineering software could be accessed by others with access to that software. Hardware (e.g., AR glasses) could be taken by someone and used to view sensitive product or customer data. The data uploaded to a cloud platform for analysis and simulation could be compromised. |
| Cybersecurity considerations |
|
As smart factory initiatives continue to proliferate, cyber risks are expected to continue to increase. As the recent study reveals, cyber preparedness of many manufacturers falls short of what is typically considered necessary to protect against not only current threats, but also new threats that could be right around the corner. An approach to mitigate these risks can be to invest in a holistic cyber management program that extends across the enterprise to identify, protect, respond to and recover from cyberattacks.
Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited, a UK private company limited by guarantee (“DTTL”), its network of member firms, and their related entities. DTTL and each of its member firms are legally separate and independent entities. DTTL (also referred to as “Deloitte Global”) does not provide services to clients. In the United States, Deloitte refers to one or more of the US member firms of DTTL, their related entities that operate using the “Deloitte” name in the United States and their respective affiliates. Certain services may not be available to attest clients under the rules and regulations of public accounting. Please see www.deloitte.com/about to learn more about our global network of member firms.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.