Brand impersonation remains one of the most effective tactics used in phishing campaigns to steal credentials or deliver malware.

By Max Gannon, Cyber Intelligence Team Manager at Cofense
When individuals receive an email that appears to come from a familiar company, they often assume it is legitimate. This false sense of security is exactly what threat actors are counting on. Brand impersonation remains one of the most effective tactics used in phishing campaigns, exploiting the trust that individuals place in companies to steal credentials or deliver malware.
However, attackers are not necessarily just casting a wide net—they are tailoring their tactics by selecting brands and spoofing techniques specific to the industry they are targeting. Over a three-year cross-industry analysis, Microsoft emerged as the top brand spoofed, accounting for a staggering 92.87% of impersonated brands. Following Microsoft were Adobe at 3.53% and Webmail at 1.61%.
While it is crucial for organizations and individuals to familiarize themselves with the common techniques used to spoof popular brands, it is equally important to recognize that specific industries are more prone to certain types of impersonation attacks.
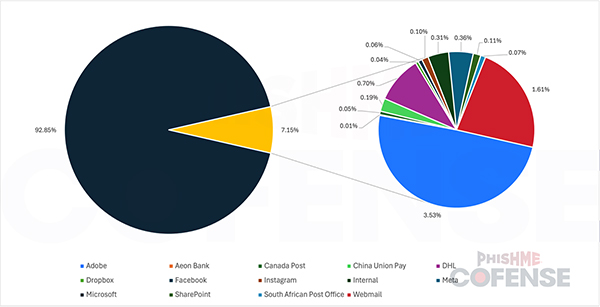
Of the 14 most commonly spoofed brands, Microsoft stood out not only for its prevalence but for the diversity of the phishing campaigns in which it was impersonated. These campaigns range from fake multi-factor authentication (MFA) notifications and shared document alerts to mailbox issues and voicemail notifications. In many cases, simply including the Microsoft logo and relevant text is enough for attackers to convince recipients of the email’s legitimacy.
Across a wide variety of industries—including finance, insurance, manufacturing, mining, retail, and utilities—Microsoft was the most frequently spoofed brand, posing a significant threat to organizations across sectors.
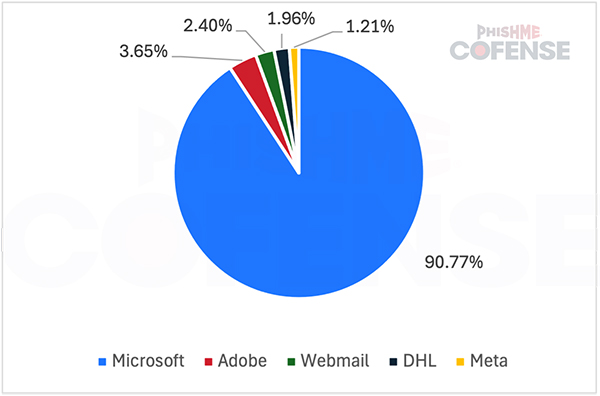
In addition to Microsoft, there are a variety of other brands that are frequently spoofed using differing tactics. For instance, phishing emails impersonating Adobe often involve fake signature requests, sometimes even linking to Adobe’s legitimate signature page, which typically will contain an embedded link to a credential phishing page.
Webmail phishing, on the other hand, represents a less sophisticated but still highly prevalent attack method. Threat actors often impersonate the victim company’s email client, particularly through low-budget or free phishing kits. While less elaborate, webmail spoofing still ranks as the third most frequent across the top 10 industries.
The techniques associated with social media brand impersonation often include policy violation notifications for Facebook and themes related to verified badges and copyright infringement for Instagram. Meta spoofing, which encompasses both Instagram and Facebook, represents some of the most convincing phishing emails, often featuring coherent narratives and believable topics. These campaigns across Instagram, Facebook, and Meta as a whole, exploit a sense of urgency, pressuring recipients to act quickly. Like Adobe, these emails will sometimes contain links to pages hosted on facebook[.]com that contain embedded links to credential phishing pages.
Microsoft and Adobe were the most spoofed brands across most top industries. The brands that follow them in frequency tend to vary by sector, reflecting the specific relationships that threat actors believe each target industry relies on. For example, in the retail sector, DHL ranked as the third most spoofed brand. This makes sense given DHL’s long-standing partnership with the retail and fashion industries. Similarly, DHL was the fourth most spoofed brand in the mining industry, where it is known for its crucial role in logistics and shipping heavy equipment.
In the real estate sector, Adobe accounted for 7.5% of spoofed brands, which is significantly higher than other industries. This reflects the frequent use of digital documents for signatures in real estate transactions and the common external sharing of Adobe documents.
Some industries had specific regional brands associated with them, for example, the South African Post Office, China Union Pay, and Canada Post. These regional brands being associated with a limited number of industries indicate that threat actors believe certain industries have more interaction with those locations than others. For example, the South African Post Office is associated with the mining industry which indicates threat actors believe mining companies are likely to have interests in South Africa.
Threat actors employ a wide range of tactics in brand-spoofing campaigns to deceive victims, including HTML file delivery, signature requests, policy violation notifications, and MFA prompts. If you can think of it, chances are, threat actors are exploiting it. Insights on the top-spoofed brands across industries help differentiate the threats each industry faces and enable more targeted mitigation strategies against phishing campaigns.
In 2023, there was a 104.5% increase in malicious emails bypassing secure email gateways (SEGs). While technical defenses are essential, they are not enough on their own—human defense is crucial. Although it may seem like common knowledge to avoid clicking on suspicious emails, the constantly evolving techniques make it difficult to always detect threats. Security awareness training is one of the most effective investments a company can make to protect its employees and, by extension, its organizational assets. As offensive AI evolves, making it easier for threat actors to launch these attacks at a larger scale, it is increasingly important for individuals to educate themselves on brand-spoofing and the tactics specific to their respective industry.

As a Senior Cyber Threat Intelligence Analyst at Cofense, Max produces tactical and strategic intelligence on phishing activity, methodologies, and motivations behind changes and evolutions in campaigns. Max specializes in phishing analysis, malware analysis, and open-source research.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.