Prevention-based security at the device level for operational resilience.
By Sagi Berco, CTO, NanoLock Security
Digital transformation and Industry 4.0 innovations are bringing unprecedented performance, agility, and efficiency to manufacturing and industrial organizations and critical infrastructure. These initiatives are bringing greater connectivity between IT and OT systems – and expanding the potential attack surface, giving more opportunities for insider and external threat actors to manipulate control systems.
Recent attacks have shown these innovations introduce new vulnerabilities, leading to safety issues, financial damages, and reputation loss. For example, a former contractor was recently charged for allegedly hacking into and attempting to delete critical software from a California water treatment facility serving 15,000 residents. In this case, protection at the device-level would have stopped him from being able to access any systems. Proactive protection at the device or asset level requires authentication and access authorization regardless of origin. In addition, device-level security must include traceability and audit capabilities to ensure operational continuity.
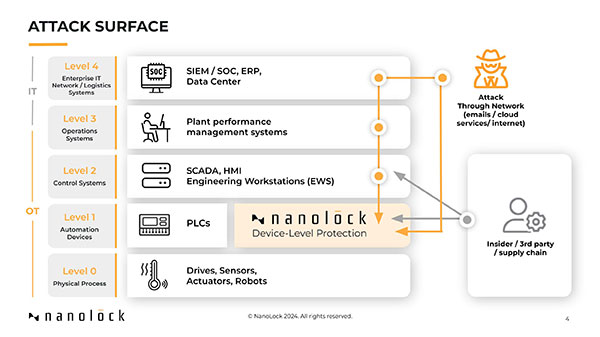
Securing operational integrity should be a top priority, with implementation of zero-trust device or asset-level protection. Using intrusion detection systems (IDS) is no longer enough. IDS merely monitor threats but fail to proactively protect attacks targeting industrial control systems. Instead, zero-trust solutions that secure the devices themselves can stop threat actors from disrupting operations.
With greater interconnectivity, organizations must prioritize operational resilience and adopt a proactive, prevention-based security approach. This means moving beyond traditional cybersecurity measures, such as IDS, and implementing robust access controls, authentication, and zero-trust principles at the device and asset level. By securing critical systems directly, organizations can prevent unauthorized access, human errors, and malicious attacks that could disrupt operations.
Today cyber security managers must understand that the human factor is a crucial element in all cyber protection efforts. Thus, companies must utilize healthy cybersecurity hygiene to mitigate the threat of human errors, which increasingly put industrial operations at risk. In 2021, the Oldsmar water treatment facility in Florida suffered an incident that was caused simply by an employee clicking incorrect buttons.
A zero-trust solution would have safeguarded the water treatment facility. Healthy cybersecurity hygiene must include device- or asset-level protection to safeguard against all threats – insiders, human mistakes, and cybercriminals.
In response to rising threats, governments worldwide are enacting stricter regulations to protect critical infrastructure. For example, the Cyber Security Agency of Singapore (CSA) introduced the Codes of Practice for Critical Infrastructure (CCoP 2.0) regulation. These guidelines urge enhanced security for essential operational technology (OT) assets. Additionally, the European Union’s NIS2 directive calls for active cyber protection and prevention capabilities, instead of just detection, to establish resilience against threats. Organizations that fail to comply with these regulations may incur heavy fines, such as €10 million under the EU’s NIS2.
What all these regulations have in common is an emphasis on strict access control, detailed activity logs, and authentication to secure critical infrastructure. These are all zero-trust philosophies, shifting cybersecurity practices from post-incident response to prevention-based. This can already be seen in the U.S., when The Environmental Protection Agency (EPA) urged public water systems to strengthen their cyber measures, asking them to meet requirements such as performing audits and regular inspections.
As the IT and OT worlds converge, it is important to keep in mind that the most common cybersecurity approach concentrates primarily on network protection. This approach is inadequate as it only addresses the connection between IT and OT. If these networks are subjected to attacks, the damage can reach further down to critical infrastructures and devices, which could have harmful repercussions on production and business.
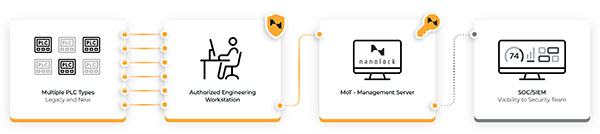
To solve this issue, many organizations air-gap their networks. This approach on its own falls short in preventing access and changes to OT assets, such as Programmable Logic Controllers (PLCs). Comprehensive protection requires securing OT assets directly instead of relying solely on segmenting or air-gapping networks. Achieving this means implementing a layered approach.
Organizations can keep their network protections, but more importantly, they must introduce device and asset level protections that follow the zero trust approach. This prevents unauthorized changes to PLCs, ensuring operational integrity and keeping production lines running. Without protecting assets at the core of the operational environment, errors and changes can still cascade from one system to another after breaching the network.

Sagi Berco has more than 20 years of experience in cyber security and technology management. Formerly, Sagi worked in the Israeli Prime Minister’s Office and took part in the development of groundbreaking systems and projects that were awarded the Israel Defense Prize.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.