New research from Arctic Wolf reveals the construction and manufacturing sectors are at an increased risk of intrusion in 2025.
By Kerri Shafer-Page, Vice President, Incident Response at Arctic Wolf
Threat actors are getting more effective at extorting their victims, largely because they’re becoming more ruthless in their tactics and techniques, and that should concern businesses of all sizes and industries without a resilient security environment. But new research from Arctic Wolf reveals the construction and manufacturing sectors are at an increased risk of intrusion and targeted more often than nearly any other industry, placing the importance proper cybersecurity measures at an all-time high.
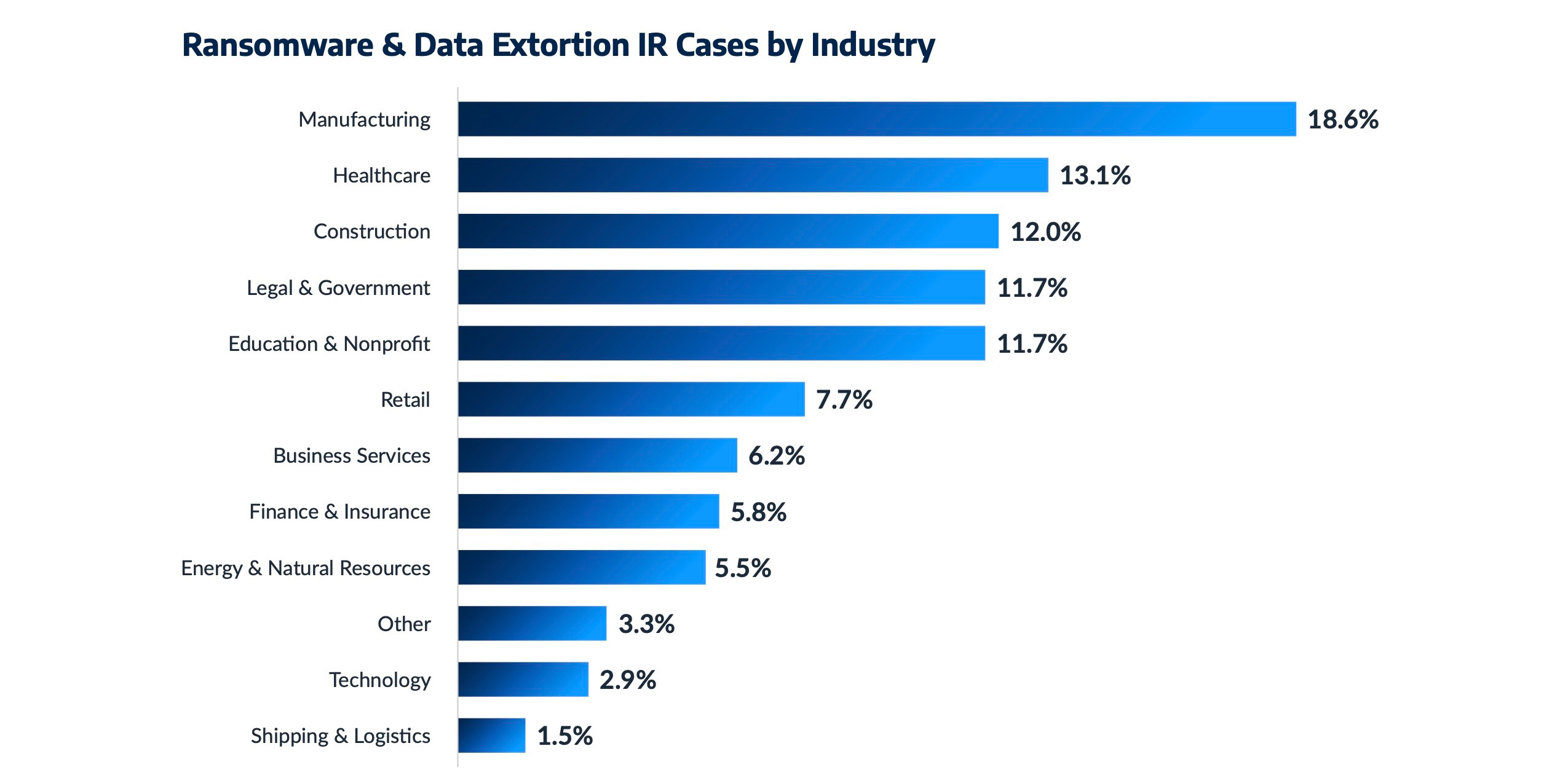
Based on research from the 2025 Arctic Wolf Threat Report that compiled data from incident response (IR) engagements, threat intelligence research, and telemetry from the Arctic Wolf Aurora Platform, the manufacturing industry was targeted by ransomware and data extortion more than any other industry, accounting for 18.6% of all cases. The construction industry was the third-most targeted, accounting for 12% of all cases, and largely for the same reasoning; ransomware operators often apply pressure to their victims by taking operations offline until a ransom is paid. In manufacturing and construction, any operational disruption is liable to derail production, risk contractual penalties, create backlogs and cause reputational damage.
Data theft from manufacturers and construction companies can also leak valuable information about their customers. Rather than simply encrypting their victim’s data, threat actors have adopted a trend of exfiltrating (stealing) it and threatening to release it as a way around the improved backup and restoration capabilities many security-conscious businesses have implemented in recent years. This kind of double extortion occurred in 96% of ransomware IR cases observed by Arctic Wolf, proving it is now the norm, not the exception, and further proving that threat actors are becoming even more ruthless.
What is interesting about the way in which threat actors target the manufacturing and construction industries is that they aren’t the two sectors that usually pay the most in ransoms — they just pay more often.
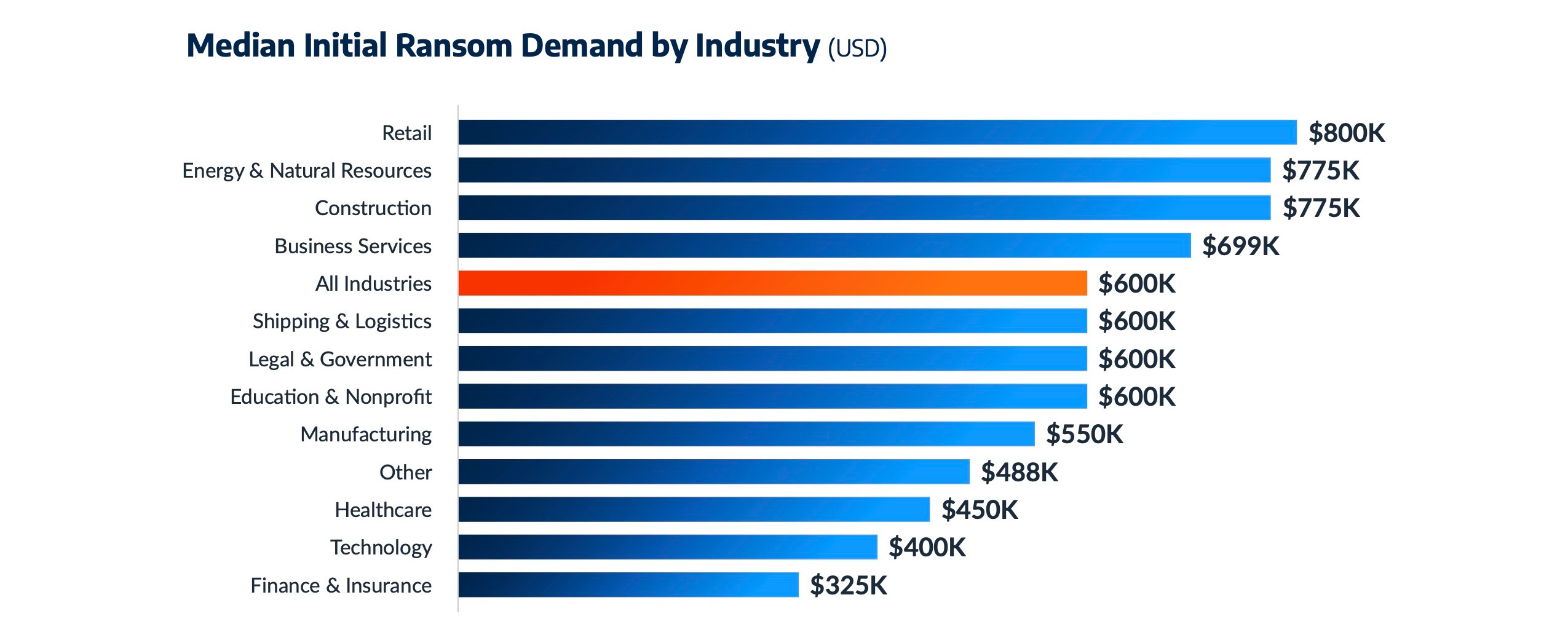
What I mean is that though the median initial ransom demand across all industries Arctic Wolf observed is $600,000, the manufacturing industry’s median demand fell below that at $550,000, while had only the third-highest median demand behind the retail and energy industries. Cyber criminals understand that a smaller, but more likely ransom payment is preferable to a less-reliable large payout. Manufacturing was in the top 3 most-targeted industries by every one of the five major ransomware groups Arctic Wolf investigated in the last 12 months, with construction also included in four of those five groups’ top three industries.
There’s no way around it; IT and security leaders at manufacturing and construction companies need to be extremely cognizant of their security posture in 2025 and beyond and now is an optimal time for those leaders to take stock of their internal security controls and their relationships with their security vendors.
Thankfully, there’s plenty of resources available to help boost resiliency, even among the most resource-strapped SMB’s. One of the first steps organizations should take is to establish, or maintain, proper backup and data storage practices. Data backups, as the Arctic Wolf threat report revealed in its findings, don’t necessarily prevent threat actors from practicing double extortion on their victims. But they do buy your organization time during the initial aftermath of a cyber-attack and prevent further ripple effects of the attack from causing problems in the future. In 68% of the ransomware incidents Arctic Wolf observed, a reliable data backup aided in the organization’s recovery process, either by granting the business more time or, in many cases, removing the need for a payout by providing an alternate path to sufficient recovery.
There’s a few principles that organizations should follow to make sure they have sufficient backups in place. The first is to adhere to the 3-2-1 principle of backup, which states that an organization should have three copies of their data, in at least two different formats of media and at least one off-site copy (ideally in a secure private cloud). Regularly testing the recovery capacity and speed of your data backups is also encouraged by security providers, because it can help iron out problems with recovery processes, prioritization or the actual backups themselves. An organization’s security vendors also likely assume some ownership of cloud and data security, so IT and security leaders need to understand exactly what elements of their security ecosystem they’re responsible for and what they can rely on their partners for.
Proper data protection and storage is essential, but there’s also foundational steps organizations can use to fortify their security, including security awareness training, identity access management controls and more. This baseline essentially looks the same for all kinds of organizations, regardless of industry, including regular security awareness training that is relevant and engaging is essential, as well as phishing-resistant multi-factor authentication. As an organization’s tech stack evolves, IT and security leaders also need to be sure of their visibility into their environment, and sure that their vendors have that same insight into potential weak spots in their ecosystem.
Vendors can also provide around-the-clock monitoring to recognize unusual user behaviors and assist in implementing zero-trust principles in an environment. These foundational steps will go a long way toward enhancing the cyber resiliency of businesses, even as cybercriminals shift their tactics and techniques.

About the Author:
Kerri Shafer-Page serves as the Vice President of Digital Forensics and Incident Response at Arctic Wolf. A proven leader in threat identification, IT security and data privacy incident response and mitigation, Kerri has served in leadership roles at IBM and AIG, overseeing incident response and cybersecurity claims.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.