The new attack vectors created by IT/OT convergence in the auto and maritime sectors underscore the need for greater collective security.
As organizations strive to become more efficient and cost-effective, the lines between information technology (IT) and operational technology (OT) are increasingly blurred. In the past, IT, which handles data processing and computing power, and OT, which deals with monitoring and controlling device performance, were largely segregated. Now, to more effectively control and monitor the complex systems from remote locations, there is a movement to consolidate IT and OT processes.
Integrating IT and OT systems has many benefits, such as reducing costs, improving visibility, and enabling more efficient asset management; however, it also can create blind spots, meaning an intrusion into one system can be a gateway into the other. While these vulnerabilities affect many industries, it has a major impact on the transportation industry.
From moving consumer goods to people to equipment, transportation is vital to the modern world, especially in the age of globalization. But as modes of transportation, like cars and ships, become more connected, their attack surface grows, thus increasing the risk of being targeted in cyberattacks.
Check out this video to learn more about IT/OT convergence and why it’s important.
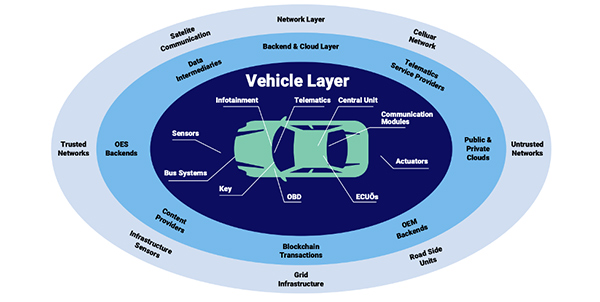
Let’s take cars, for example. We are now seeing a movement toward “connected cars,” which are essentially any cars that connect to the internet. Connected vehicles can now download software updates, access and send data, connect with other devices, and may soon be able to even drive and park themselves.
But while connected cars offer improved functionality, they also open the door to a plethora of attack vectors that hackers – with varying levels of skills and resources – can exploit.
This fear first came to light in 2015, when two researchers successfully hacked a moving car and took control of the brakes, accelerator, and even the windshield wipers – all from a computer 10 miles away. They did this by moving laterally and exploiting the lack of separation between the different onboard systems.
This is why “security by design” needs to be the motto for the automotive industry. The security of vehicles must be an essential part of the car’s design rather than an afterthought. If car suppliers and manufacturers integrate security measures – like segmentation, encryption, and access control – from the get go, they will be able to avoid a lot of problems down the road (both metaphorically and physically).
As the backbone of the global economy, maritime transportation accounts for an estimated 90% of world trade. For this reason, the lagging cybersecurity of many ship systems and the ease of hacking into said systems pose a significant threat to the global supply chain.
Think about important maritime chokepoints, like the Suez Canal. When the Ever Given got stuck in the Suez Canal for six days in March, we saw the catastrophic impact such an obstruction can have on world trade. Though this was not the result of a cyber intrusion, it demonstrated to threat actors the potential for disruption if they can gain access to large vessels’ navigation and/or steering systems.
Though naval vessels are historically uncommon targets for cyberattacks, their growing use of industrial control systems (ICS) and satellite communications have made cyberattacks against OT on ships the norm rather than the exception.
For nation-states, the ability to manipulate commercial and government-owned ships offers many political and economic benefits, and finding weaknesses in the abysmally insecure maritime cyber environment is not very difficult. The internet protocol networks used for navigation and steering are often not compartmentalized effectively, and as ships and systems increasingly rely on automation, the risk of cyberattacks grows.
The process of compromising a maritime vessel is arguably very simple, at least it was during the HackTheSea challenge at the August 2021 DefCon cybersecurity conference. In the simulated challenge, it took skilled teams less than 14 hours to penetrate the ship’s onboard navigation system and move laterally across the networks to gain control of vital systems, like the steering and throttle.
In order to fortify the security of ships, preparation is key. Maritime companies need to conduct a thorough risk analysis to understand the consequences of maritime cyber threats, and they also need to develop robust contingency plans to ensure operational continuity in the case of an attack. For more comprehensive guidelines on how to improve the operational resilience of maritime vessels, refer to these high-level recommendations provided by the International Maritime Organization (IMO) on cyber risk management.
Attacks on any form of transportation are regarded as attacks on critical infrastructure. Therefore, many governments and international bodies have already set up regulations to establish cybersecurity baselines for various forms of transportation. However, this trend to develop more clear frameworks for designing, constructing, and maintaining transportation systems must continue.
Industries need to collectively strengthen the cybersecurity of the automobile and maritime subsectors, as this will be critical to preventing the future exploitation of vital transportation systems. In the past, isolating and air gapping OT networks might have sufficed, but this movement toward converged systems requires an interconnected security fabric that responds to events in real time, makes autonomous decisions, and collectively shares information with a larger community to alert other systems in the case of a cyberattack.

About the Author:
Morgan Demboski is a Threat Intelligence Analyst for IronNet Cybersecurity and is currently pursuing a Master’s degree in Intelligence and Security Studies and a Graduate Certificate in Intelligence Analysis through The Citadel in Charleston, SC. She is also Co-Director of Communications at The Prosecution Project (tPP), a project investigating how political violence is prosecuted in the U.S. She graduated from Miami University in May 2020 with a Bachelors in Social Justice Studies (concentration in Crime & Law) and a minor in Political Science.
Contact:
Linkedin: https://www.linkedin.com/in/morgandemboski/
Twitter: https://twitter.com/MorganDemboski
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.