Honeywell’s 2025 Cybersecurity Threat Report revealed a sharp rise in malware, but a Zero Trust architecture can help protect operations.
By Paul Smith, director of Honeywell Operational Technology Cybersecurity Engineering
It’s any plant manager, CIO or company president’s biggest nightmare.
One morning, your biggest plant is surpassing its production goals and the company is on target for an excellent financial quarter. Then, suddenly, assembly operations unexpectedly grind to a halt. A supervisor rushes in saying the control systems have gone down and a computer lockout message is demanding a $20 million ransom to restore operations.
This scenario is happening more frequently at plants and supply chains of all industries, including everything from automotive factories to refineries to public utilities. And even when companies avoid serious outcomes such as production interruptions or ransom demands, malware infections continue to rise and await a moment of opportunity.
All of this adds up to a very disruptive and expensive problem. Industry reports show that unplanned downtime, caused by cybersecurity attacks and other issues like equipment failure, costs Fortune 500 companies approximately $1.5 trillion annually. This stunning amount represents almost 11% of their total revenue.
Governmental research, Honeywell and other cybersecurity companies have been sounding the alarm on growing and increasingly sophisticated cyber threats against the industrial sector for years. For example, the Cybersecurity and Infrastructure Security Agency (CISA) in the U.S. has been issuing a growing number of alerts and advisories to notify organizations about new vulnerabilities. An article last year in Industry Today reported that 35% of all cyber-espionage attacks target the manufacturing sector.
This year, Honeywell’s 2025 Cybersecurity Threat Report revealed that malware and ransomware increased significantly from Q4 2024 to Q1 2025, with ransomware attacks jumping by 46% during the quarter. For the report, Honeywell’s research team analyzed more than 250 billion logs, 79 million files and 4,600 incident events that were blocked across Honeywell’s global install base. The data revealed that 2,472 potential ransomware attacks were documented in Q1 2025. This data clearly showed an escalation in ransomware, as attacks during the first three months of 2025 had already reached 40% of the annual totals recorded in 2024.
While the profiles of attackers vary, including everyone from lone wolves to anarchists to foreign criminal groups, one of the most common motives involves extorting money from organizations. Industrial operations across critical sectors like energy and manufacturing make very attractive ransomware targets because they must avoid unplanned downtime as much as possible. But no industries are being spared, with attacks cropping up across all sectors – from energy and manufacturing to agriculture and food production.
One of the more alarming findings revealed that, as attackers quickly evolve, they are now leveraging ransomware-as-a-service kits to compromise industrial operations. The data found a 3,000% spike in the use of one trojan designed to steal credentials from industrial operators. The dangerous W32.Worm.Ramnit trojan accounted for 37% of files blocked by Honeywell’s Secure Media Exchange (SMX).
For a number of years, organizations have isolated their Operational Technology (OT) assets from their IT networks. While a majority of these OT assets run on older computer systems, which make them vulnerable to malware, many companies “air gapped” and isolated them from networks to further protect the systems from intrusions.
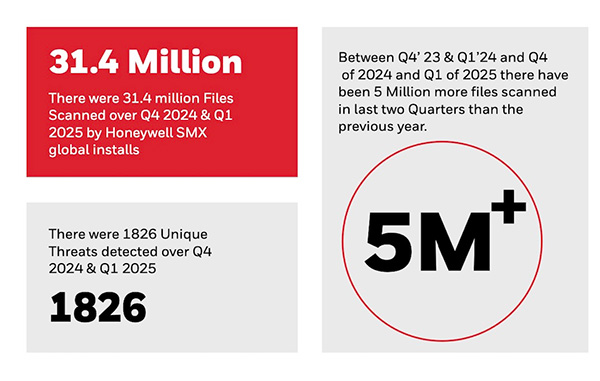
Just like homes, every operating system has a door. They can be either virtual with a network, or physical with a drive. Most OT systems use a USB drive mainly for plug-in software updates. For this reason, USB devices continue to be a persistent vector for introducing malware. In Q1 2025, Honeywell detected 1,826 unique USB threats via SMX, with 124 never-before-seen threats. This uptick built on years of continued growth, with a 33% increase in USB malware detections in 2023, following a 700% year-over-year surge in 2022.
However, USB drives are not the only way intrusions continue to succeed. The 2025 Cybersecurity Threat report expanded its analysis this year to include threats delivered through additional plug-in hardware – known as Human Interface Device (HID) – including mice, charging cords for mobile devices, laptops and other peripherals often used when updating or patching software for on-premise systems. Unfortunately, cybercriminals now engineer some of these devices to be intentionally and unintentionally introduced into the OT environment of many unsuspecting organizations.
Even if an organization has the best training for employees to avoid these types of devices, compromised vendors or suppliers can introduce malware into an air-gapped environment through legitimate access points. And evolving attacks continue to grow. Some sophisticated hackers are now leveraging signals and electromagnetic emanations (EMRs) from USB devices to steal data from these air-gapped systems.
Despite the growing amount of cybersecurity threats, there are some minimum steps organizations can take now to protect their operations and people.
First, leadership should ideally review their cybersecurity policies and procedures monthly. Developing and following cybersecurity policies and standard operating procedures can streamline threat identification, detection and response to threats. They can also reduce delays and damage when an attack occurs.
Second, all companies should deploy a Zero Trust architecture that assumes no implicit trust between systems. Every user, device and workload accessing an OT environment must be verified. Implement least privilege access so that users, devices and applications only have the necessary access to perform their tasks, lowering the potential for a breach. Use strong passwords, multi-factor authentication (MFA) and password vaults to prevent rogue access to devices.
Third, organizations should regularly update software to fix vulnerabilities and invest in strong threat detection capabilities. This includes ensuring all removable media and USBs are scanned with products from approved vendors. Systems should be isolated to reduce the risk of viruses spreading during a cybersecurity attack.
Lastly, it’s critical to educate employees on how to identify and avoid threats such as phishing and malware. Teaching good cyber hygiene practices can go a long way to help reduce the overall risk of malware and ransomware in this elevated threat environment.
Cyber threats are evolving fast, but so are the defenses. Companies that act now by deploying Zero Trust, training their teams and securing every access point will strengthen operational resilience. Now is the time to turn cybersecurity into your plant’s strongest shield.

About the Author:
Paul Smith is director of Honeywell Operational Technology (OT) Cybersecurity Engineering. He also authored Honeywell’s 2025 threat report. Learn more about Honeywell’s OT cybersecurity solutions at https://www.honeywell.com/us/en/company/ot-cybersecurity.
Read more from the author:
Pentesting Industrial Control Systems: An ethical hacker’s guide to analyzing, compromising, mitigating, and securing industrial processes | December 2021
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.