Key takeaways from the sixth annual Fortinet State of OT and Cybersecurity Report.
By Richard Springer
Many organizations continue to struggle to secure their operational technology (OT) environments. The Fortinet 2024 State of Operational Technology and Cybersecurity Report reveals a concerning rise in cyberattacks targeting OT systems. Based on a global survey of more than 550 OT professionals, the report found that 73% of organizations experienced intrusions affecting their OT systems in 2024, representing a significant increase from 49% in 2023.
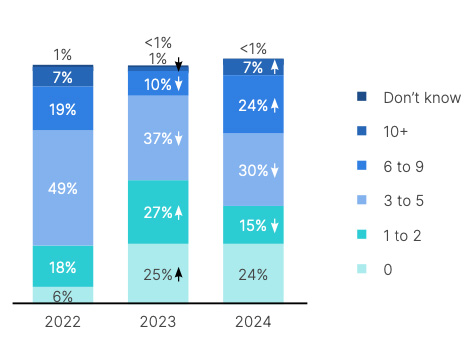
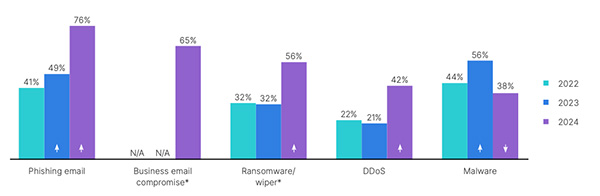
Key findings from the report include a surge in OT system breaches, with nearly three-fourths of organizations experiencing intrusions affecting either OT systems alone or both IT and OT systems. The frequency of these attacks is also increasing, with 31% of respondents reporting more than six intrusions in the past year, compared to just 11% in the previous year. Ransomware and wiper attacks, in particular, have seen a significant rise, impacting 56% of respondents, up from 32% in 2023.
The report also highlights the struggle organizations have in keeping up with today’s evolving threats. The percentage of organizations that have complete visibility over their OT systems within their central security operations dropped from 10% to 5%, although those reporting 75% visibility increased. This change suggests a growing awareness of the complexities of OT security and a more realistic understanding of existing security postures.
Unlike traditional IT environments, OT faces threats from traditional ransomware aiming to disrupt critical infrastructure and OT-specific malware, often designed by nation-state actors, targeting physical processes. Key challenges to properly security OT environments are because of older equipment that wasn’t designed with security in mind and the unique communication protocols used in OT, which often are difficult to integrate with other security tools.
In response to these challenges, organizations are increasingly prioritizing OT security. The report notes a shift in responsibility for OT security toward C-suite roles, with over 60% expected to take charge in the next year. Where the CIO isn’t directly responsible, the responsibility moves from the network engineering director to the vice president of operations. This shift underscores the growing recognition of OT security’s importance at higher management levels.
The report emphasizes the need to take a multi-faceted approach to OT security. It includes advice for improving IT and OT network protection by adopting the best practices outlined in the 2024 State of OT and Cybersecurity Report.
Many organizations are adopting a phased approach to modernize OT security based on the best practices focusing on visibility into devices and network traffic, segmenting OT networks, implementing zero trust principles, and deploying advanced security monitoring and response capabilities.
However, the report also showed a concerning trend in OT security maturity levels. In 2022, 13% reported 100% visibility, but this number dropped to 10% in 2023 and further decreased to 5% in 2024. These changes suggest that, as organizations mature, they become more aware of blind spots, leading to a more realistic assessment of their visibility. However, there’s growth at both ends of the spectrum: basic visibility and segmentation are increasing, as is the adoption of advanced orchestration and automation.
After six years of surveying OT professionals, it’s encouraging that OT cybersecurity has gained the attention of C-suite executives and enterprise leadership teams. But it’s also clear that OT organizations still have a lot of cybersecurity work to do going forward.
To learn more about the current state of OT and the best way to meet today’s OT cybersecurity challenges, download the full report.

Rich Springer is the director of OT solutions marketing at Fortinet. In this role, Rich works alongside regional marketing teams, OT product management, and OT threat researchers to promote the Fortinet Fabric of OT Solutions, including network security, zero trust, security operations, and AI-powered threat intelligence for IT-OT converged and OT market segments. Previously, Rich was the head of industrial cyber strategy and development for Tripwire, managing Belden’s Industrial cyber product business, including the Hirschmann and Tripwire product lines. While evolving in the cybersecurity software and hardware development business, Rich provides an operational background as a prior global head of SCADA in wind energy and across various roles in the semiconductor industry and the submarine nuclear Navy.
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.