Practical considerations when managing cyber risk and preventing the theft of Intellectual Property.
Last month, a former lead scientist of glass manufacturer Corning was indicted for stealing trade secrets relating to a DARPA collaboration. While Corning may be able to successfully pursue legal compensation, by the time that rogue employee had exfiltrated critical business data and shared with international competitors, the damage had already been done. Exacerbated by the vast amount of data the average manufacturer is tasked with managing, the threat of insider theft today is more relevant than ever. The past year has already seen the manufacturing industry face an unprecedented wave of cybercrime, with one threat report finding cyberattacks on the industrial sector have spiked 91% in the past year. This unfortunate trend is not likely to reverse any time soon. Another report from Deloitte finds that nearly 50% of manufacturing executives lack confidence that their firms are protected.
Attention paid to the rise of cybercrime in the industrial sector has mostly been driven by large scale attacks on the supply chain, such as the recent ransomware attack on Colonial Pipeline. While ransomware attacks like these have frightening implications for business leaders, who fear the obvious financial implications of a critical attack that can cripple operations, these attacks can also serve as a wake-up call. While concerned organizations may imagine that a successful breach or cyber attack will usually result in a business-halting ransomware incident, the reality is that most cybercrime will go undiscovered, resulting in the ongoing leak of critical information. The 2020 Verizon Data Breach Investigations Report finds that internal errors and abuses, like accidental misconfigurations or privileged access misuse, now account for more breaches than malware.
Though many manufacturers respond with increased cybersecurity investment, the concern of insider threats are still often not prioritized. The FBI estimates that cyberattacks targeting IP and critical business data cost US businesses alone up to $600B a year. Industry leaders across the manufacturing sector rely on their trade secrets to maintain a competitive edge. Without proper data security and privileged access measures in place, manufacturers will continue to face the fallout of unmitigated insider threats, theft of intellectual property and resulting impact to their bottom line.
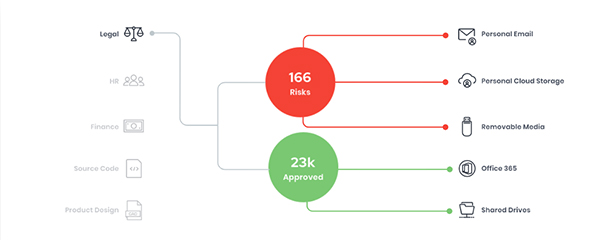
Still, manufacturers too often treat the threat of internal misappropriation as an afterthought. To protect proprietary data, manufacturers must develop a cybersecurity program that actively manages the risk of insider threats. Managing huge quantities of data transfer is an unavoidable reality for firms supporting the supply chain, and a good risk assessment plan should understand this to avoid friction. A nuanced approach requires firms to review their data flows to confirm where information should and shouldn’t be going.
Crucial to this is developing a low-friction method of tracking the firm’s data lifecycle which still enables employees to engage in secure best practices. Rather than, for example, generically flagging or blocking users who misstep – by maybe sending a report to their personal email when faced with a technical limitation with corporate approved cloud services – a well-rounded approach should seek to intelligently track and understand how users regularly interact with business data to determine what is expected and identify risky and/or unexpected user behaviors.
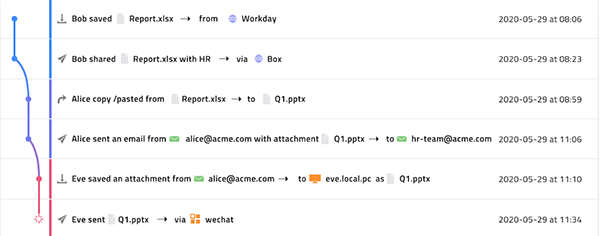
Third-party risk assessments are often a necessary and required aspect of enabling this wide scale level of intelligent data management, but accomplishing a holistic understanding of the digital environment will not come with a single point-in-time assessment. To properly detect and react to any threat as it occurs, manufacturers must pursue third-party tools which are able to continuously examine data movements in their environment. Of course, these tools will themselves be in constant contact with high-risk or sensitive data, so manufacturers must turn to third-party vendors who are regularly conducting their own internal risk assessments. To ensure that these assessments do not endanger the very data it attempts to analyze, manufacturers should look to vendors who provide regular audits and proof of compliance.
An intelligent and comprehensive understanding of the flow of data, once established, will better enable these continuous risk assessments. By tracking the full lifecycle of data, manufacturers should be able to visualize their greatest areas of risk. In profiling risk, firms should determine which datasets are high-value, which datasets are public facing and which datasets are widely exchanged throughout the organization. Firms can be more prepared to efficiently implement appropriate protections if they’re enabled to more efficiently implement appropriate protections and eliminate or mitigate their most pressing threats.

Howard Ting is CEO of Cyberhaven, creating the world’s first Data Detection and Response (DDR) platform. Cyberhaven enables organizations to secure and track all data movement by users in order to prevent data breaches and malicious exfiltration. With experience scaling industry-leading cybersecurity firms, Howard is eager to help businesses transform the way they see their data and protect their valuable IP.
Contact Information:
www.cyberhaven.com
Email: Cyberhaven@luminapr.com
Scott Ellyson, CEO of East West Manufacturing, brings decades of global manufacturing and supply chain leadership to the conversation. In this episode, he shares practical insights on scaling operations, navigating complexity, and building resilient manufacturing networks in an increasingly connected world.