As critical infrastructures navigate ongoing cyber threats, manufacturing faces increased pressure to strengthen its cyber risk posture.

By Donovan Tindill, Sr Director, OT Cybersecurity, DeNexus
The manufacturing industry faces constant threats from cyberattacks due to its reliance on complex supply chains, a patchwork of business applications, and multiple generations of industrial control systems (ICS) to manage high-value manufacturing processes. Attacks on IT networks can propagate to adjacent Operational Technology (OT) environments for manufacturing, further increasing the risk levels for production lines.
All these elements produce critical dependencies that can elevate the dangers of cyberattacks and insurance claims for manufacturers. For this reason, OT managers, facility directors, and IT teams need to develop models that can prioritize their shared security investments by rating which sites and facilities are most vulnerable to cyberattacks.
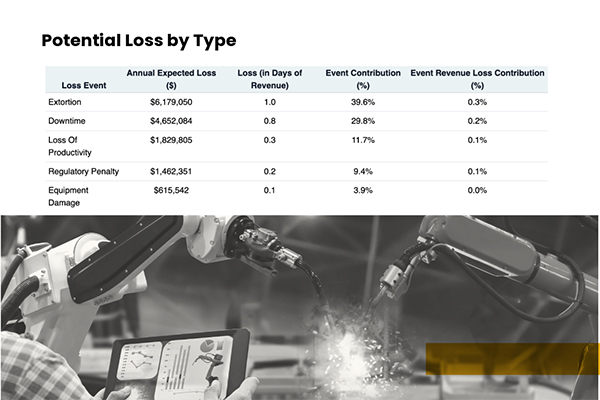
This modeling process starts by identifying the greatest cyber risks based on the probability and severity of cyber events against each facility’s OT environment based on existing controls and identified vulnerabilities. In this way, CISOs and CFOs can compare the impacts of various loss drivers, and then measure their risks in financial terms. Such analyses also allow cybersecurity leaders to communicate cyber risks in ways that empower financial decision-makers to manage cyber risks alongside other business risks.
Past conventional approaches have assigned a criticality rating to each OT cyber asset by evaluating the severity of identified vulnerabilities if any. But those metrics, or scores, often fall short in persuading financial decision-makers. Instead, the clearest way to promote cyber risk investment is by quantifying cyber risks in terms of their bottom-line costs or savings. New software platforms for cyber risk quantification and management provide tools to measure such risks and weigh potential financial outcomes.
By demonstrating that an investment of X can substantially reduce the probable loss by Y, manufacturers can create a solid foundation for cyber risk management. This shift from a purely technical justification to a more financially oriented perspective helps make the case for cybersecurity investments, while supporting strategic decision-making with a strong fiscal rationale.
The interconnectivity of the industrial ecosystem is undergoing a rapid transformation stemming from the use of artificial intelligence (AI) in more equipment, sensors, smart products, and the expansive Internet of Things. Yet nearly half of cyber risk executives in the manufacturing industry have said they lack confidence that they are protected from cyber risk, while 48% said they lack adequate funding for security, according to a Deloitte survey.
The top three desirable cyber initiatives cited by manufacturing executives included enterprise cyber risk assessments, data loss prevention programs, and increased employee training and awareness. In that spirit, here are several specific steps that manufacturers can take to reduce their exposure to OT cyber risks and secure their ICS:
Implement Cyber Risk Assessments. Almost one-third of manufacturers (31%) have not performed cyber risk assessments on the ICS in their facilities, according to Deloitte. And nearly two-thirds of companies that have performed an ICS cyber risk assessment used internal resources, potentially introducing organizational bias into the assessment process. Independent third-party enterprise risk assessments should be shared with the board to show potential impacts and business outcomes in terms of data protection, industrial control systems, and connected products.
Create an Inventory of All Connected Devices. This holistic list should include any ICS components that are attached to network segments. Such inventories of assets can be gathered through a combination of passive scanning and active observation.
Build a “Zero Trust” Network. The watchwords of “never trust, always verify” should extend to all parts of a manufacturing organization. This strict approach to security reduces the exposure of vulnerable systems, including ICS. It also segments systems to reduce the likelihood of lateral movements across network connections in the event of a breach.
Form a Cross-Functional Security Team. Such teams should include representatives from global information security, engineering, operations, and the control system vendor. Bringing all these relevant groups together can improve an organization’s ability to respond to risks. Such collaborations also increase visibility into the overall decision-making process across departments.
Engage the Board and C-Suite. Launch a senior-level management committee, including some board members, to develop a business-driven cyber risk management program. Board members should also review cyber breach incident management frameworks to develop escalation criteria.
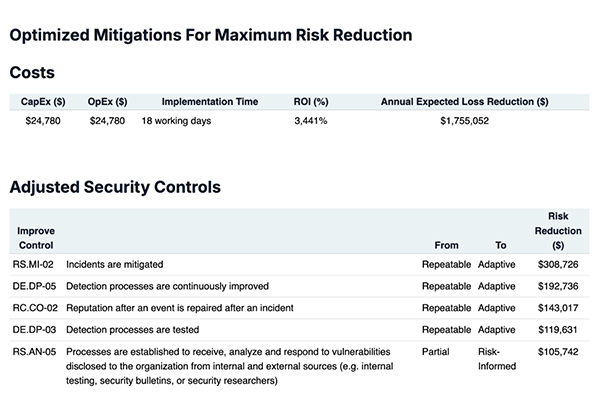
To supplement these steps, an important strategy for improved resilience involves the use of emerging technologies to build closer ties between the C-suite, board members, and security managers at manufacturing facilities. New software platforms have incorporated AI and machine learning (ML) to specifically anticipate and mitigate cyber risks for the manufacturing sector.
These systems ingest manufacturing data and OT metrics to deliver deep insights into the cyber risk profile of production sites, creating a financial snapshot from the results. Metrics such as production efficiency ratios, equipment downtime percentages, and supply chain throughput rates provide nuanced insights to help bridge the security gap between IT and OT.
A clever what-if analysis can transform insights into measurable business outcomes. By applying AI, ML, and probabilistic inference, these systems can crunch huge sets of data to determine, for example, how much cyber risk is being carried on the manufacturing balance sheet. Or they can measure the efficiency of cybersecurity programs to prioritize the most pressing risk mitigation projects.
This innovative approach to risk management can help manufacturers achieve their organizational objectives for risk tolerance at last, while promoting an elevated security posture that ultimately aligns the security leadership with the financial management side of the business.

About the Author:
Donovan Tindill has over 20 years of experience dedicated to industrial control systems (ICS) and operations technology (OT) cybersecurity. Donovan advances industrial cybersecurity globally by volunteering to teach, contribute to standards, support conferences, and serving as a thought leader. He spent over 17 years customer-facing as a control systems cybersecurity consultant in Canada, training and mentoring the technical team, leading major projects, and driving consulting services growth and innovation. He was a former ISA-99/62443 trainer, working group co-chair, and contributor. He is on the steering teams for both US CISA ICSJWG as Vice-Chair and Public Safety Canada ICS Symposium, helping select speakers, drive awareness, and knowledge about ICS/OT cybersecurity. Donovan leads the OT cybersecurity discipline from within the product team at DeNexus.
Tune in for a timely conversation with Susan Spence, MBA, the new Chair of the ISM Manufacturing Business Survey Committee. With decades of global sourcing leadership—from United Technologies to managing $25B in procurement at FedEx—Susan shares insights on the key trends shaping global supply chains and what they mean for the manufacturing outlook.